Use one of these specialised builds that go one step further than your favourite distribution’s security policies and mechanisms
Table of Contents
[sc name=”ad 2″]
Kodachi Linux
This Debian-based project aims to equip users with a secure, anti-forensic and anonymous distribution. It uses a customised Xfce desktop in order to be resource-efficient and claims to give users access to a wide variety of security and privacy tools while still being intuitive. www.digi77.com/linux-kodachi
Qubes OS
Endorsed by Edward Snowden, Qubes enables you to compartmentalise different aspects of your digital life into securely isolated compartments. The project makes intelligent use of virtualisation to ensure that malicious software is restricted to the compromised environment. www.qubes-os.org
Subgraph OS
This is another distribution on Snowden’s watchlist. Subgraph is a relatively new project that works its magic by building sandbox containers around potentially risky apps such as web browsers. Despite its stability its developers are calling it an alpha release. https://subgraph.com
Whonix
This Debian-based distribution is unlike any of its peers that install and run atop physical hardware. Whonix is available as a couple of virtual machines that can run over KVM, VirtualBox and even Qubes OS. This unique arrangement of virtual machines also helps ensure your privacy. www.whonix.org
Kodachi Linux
A reasonably secure distribution – easy to use but difficult to install

Kodachi enables you to use your own VPN instead of Kodachi’s and will ban users who misuse their VPN for things such as hosting illegal torrents
How is it secure?
Unlike some of the other distros, Kodachi doesn’t use a hardened kernel. However the kernel is patched against several denial of service and information leak vulnerabilities, and also the major privilege escalation vulnerability Dirty COW. It also includes Firejail to run common applications inside sandboxed environments.
What about anonymity?
Kodachi routes all connections to the internet through a VPN before passing them to the Tor network. It also bundles a collection of tools to easily change identifying information such as the Tor exit country. Additionally, the distribution encrypts the connection to the DNS resolver and includes well-known cryptographic and privacy tools to encrypt offline files, emails and instant messaging.
Useful as a desktop?
The distro is loaded to the brim with apps that cater to all kinds of users. Kodachi includes all the apps you’ll find on a regular desktop distribution and then some. Its hefty 2.2GB Live image includes VLC, Audacity, LibreOffice, VirtualBox, KeepassX, VeraCrypt and more. There’s also the Synaptic package manager for additional apps.
Installation and setup
This isn’t one of the distribution’s strong suits. Kodachi uses the Refracta installer to help anchor the distro. However the installer is very rudimentary; for instance, it uses GParted for partitioning the disk. You also can’t change the default username because then many of the custom scripts won’t function post-installation – not something we’d expect to see.
Overall
Kodachi uses Firejail to sandbox apps and isn’t very easy to install. But its collection of privacy- centred tools and utilities that help you remain anonymous when online is unparalleled.
8
Qubes OS
Ensures maximum security and privacy, but at the price of usability
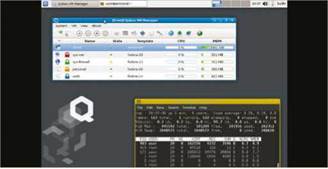
Qubes OS has an easy to follow installer, but it is a complicated distro and you need to learn the ropes. (See LU&D189 p60 for a detailed guide.)
How is it secure?
Qubes divides the computer into a series of virtual domains called qubes. Apps are restricted within their own qubes, so you run Firefox in one to visit untrusted websites and another instance of the browser in a different qube for online banking. A malware ridden website in the untrusted qube will not affect the banking session.
What about anonymity?
Qubes is geared more towards security rather than privacy and anonymity, and therefore doesn’t include any specific software or integrated processes to hide your identity. In fact, if you care about privacy as well as security, Qubes’ developers suggest running Whonix on top of a Qubes installation to get the best of both worlds – though obviously performance will suffer.
Useful as a desktop?
Qubes functions pretty much like any Fedora-based distribution, but you’ll need to familiarise yourself with its peculiarities. For example, you can add additional apps with dnf or a graphical app but you’ll need to make sure you do this within TemplateVM. If you aren’t careful you’ll end up negating Qubes’ security advantages.
Installation and setup
Qubes is available as an install-only medium. The project developers don’t recommend installation on a dual-boot computer, nor inside a virtual machine such as VirtualBox. It uses a customised Anaconda installer which is a breeze to navigate. However, if your graphics hardware isn’t detected the installer falls back to the command-line installer which has a well-known bug that prevents installation.
Overall
Qubes compartmentalises the entire Linux installation into Xen-powered virtual domains.
This arrangement ensures that a compromised app doesn’t bring down the entire installation.
7
Subgraph OS
Manages to successfully tread the line between usability and security
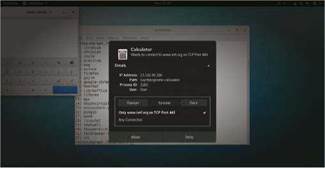
You can use the intuitive Subgraph Firewall to monitor and filter outgoing connections from individual apps
How is it secure?
Subgraph ships with a kernel hardened with the PaX set of patches from the Grsecurity project that make both the kernel and the userland less exploitable. The distribution also forces users to encrypt their filesystem. To top it off, Subgraph runs many desktop applications inside the Oz security sandbox to limit the risks.
What about anonymity?
The distro anonymises all your internet traffic by routing it via the Tor network. It also uses the anonymous, peer-to-peer file sharing application OnionShare. Then there’s Subgraph Firewall, which applies filtering policies to outgoing connections on a per-application basis and is useful for monitoring unexpected connections from applications.
Useful as a desktop?
Subgraph includes a handful of mainstream apps for daily desktop use, such as LibreOffice and VLC. On Subgraph these come wrapped by the sandboxing system Oz for added privacy protection. The distribution is also configured to fetch packages from its own custom repository and that of Debian Stretch.
Installation and setup
Subgraph uses a modified Debian installer to help you set up encrypted LVM volumes during installation. The distribution establishes a connection to the Tor network as soon as it’s connected to the internet – but it doesn’t include the Tor browser by default, which is automatically downloaded when launched for the first time.
Overall
Subgraph goes to great lengths to ensure everything from the kernel to the userland utilities aren’t exploitable. It also bundles a host of privacy- centred apps along with mainstream desktop apps.
8
Whonix
A ready-to-use OS that’s available as two KDE-powered virtual machines
The iptables rules on the Whonix-Workstation force it to only connect to the virtual internet LAN and redirect all traffic to the Whonix-Gateway
How is it secure?
Built on the concept of security by isolation, Whonix comes in the form of two virtual machines. The idea behind this is to isolate the environment you work in from the internet access point. On top of this, Whonix routes all internet traffic through Tor. Thanks to this, even if one of the machines is compromised, it wouldn’t affect the other.
What about anonymity?
Whonix uses Tor to hide your IP address and circumvent censorship. The distribution also bundles the anonymous peer-to-peer instant messenger Ricochet and the privacy-friendly email client combo of Thunderbird and TorBirdy. Whonix doesn’t includes Tor by default, but there’s a script to download a version from a list of stable, new and hardened releases.
Useful as a desktop?
Whonix doesn’t include LibreOffice but does have VLC. There’s also KGpg for managing keys, and many of its applications are tuned for privacy. The distro has a bunch of repos and you’ll have to choose one while setting it up. It doesn’t include a graphical package manager, but you can use the WhonixCheck script to search for updates.
Installation and setup
There’s no installation mechanism for Whonix. Instead, the project’s website offers several deployments mechanisms, the most convenient of which is to grab the VMs that work with VirtualBox.
At first launch, both VMs take you through a brief setup wizard to familiarise you with the project and to set up some components, such as the repository.
Overall
Whonix is a desktop distro that’s available as two separate VMs. It ensures security and privacy by using a virtualisation app to isolate the work environment from the one that faces the internet.
8
In brief: compare and contrast our verdicts
| Kodachi Linux | Qubes OS | Subgraph OS | Whonix | |||||
| How is it secure? | Uses a patched kernel instead of a hardened one and sandboxes apps with Firejail | 8 | Uses Xen to divide the desktop and apps into virtual ‘qubes’ that are isolated from each other | 9 | Includes a hardened kernel and runs many common apps inside a security sandbox | 9 | Isolates the internet gateway from the workstation in which you run your apps | 8 |
| What about anonymity? | Routes all connections to the internet first via a VPN and then through the Tor browser | 9 | Its architecture ensures a certain level of privacy but that’s not intended to be its forte | 5 | Routes all traffic through Tor and comes bundled with a host of privacy- centred apps | 9 | Routes all traffic via Tor and includes a good many useful privacy apps and utilities | 8 |
| Useful as a desktop? | The Xfce desktop is loaded with marquee open source apps for all kinds of users | 9 | It operates like any other Fedora installation, so long as you adhere to its specific nuances | 6 | Bundles a few mainstream apps but can be fleshed out via its own and Debian’s repos | 8 | Its KDE desktop is limited and you’ll need to add extra apps from the command line | 7 |
| Installation and setup | Uses the rudimentary Refracta installer which is Kodachi’s weakest aspect. | 5 | Install-only distribution that uses a modified but easy-to-operate Anaconda installer | 8 | Uses a modified Debian installer and doesn’t require much setting up before use | 8 | Ships as two VMs that you simply import into an app such as VirtualBox and boot | 9 |
| Overall | Uses Firejail to secure its collection of apps but is cumbersome to install | 8 | Ensures compromised applications don’t make the entire distro installation vulnerable | 7 | Provides a secure environment with a collection of apps to safeguard your privacy | 8 | An easy-to-deploy distribution that uses virtualisation to ensure security and privacy | 8 |
AND THE WINNER IS…
Qubes OS
There’s very little to choose between the contenders, with all of them doing their bit to protect users from vulnerabilities and exploits. Linux Kodachi and Subgraph OS are pretty similar in that both use sandboxed environments to isolate applications from each other and limit their footprint on a system, which makes them some of the best means to shield your data. Both projects also make good use of the Tor network to help their users remain anonymous online.
The main reasons for Kodachi’s elimination are that it doesn’t use a hardened kernel and it isn’t easy to install. These problems don’t exist in the Snowden-endorsed Subgraph, which is steered by a team of developers with a proven track record of developing security- centred apps.
Subgraph also doesn’t have the same steep learning curve as some of its peers and offers far better protection than a regular desktop distribution. However, many security engineers have pointed out security and privacy leaks that make it less secure than our winner. Even its developers accept that Subgraph needs improvements.
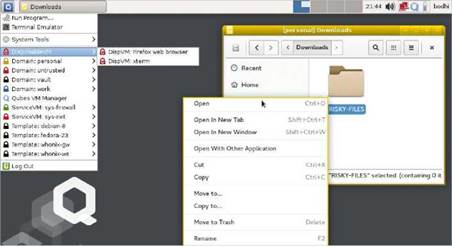
Open unfamiliar files in a DisposableVM to make sure they don’t compromise the rest of the
This leaves us with Whonix and Qubes. Whonix is more geared towards privacy, while Qubes is designed to be a comprehensive secure OS. They are the two most innovative and technically superior options of the lot, though at the same time are also the most cumbersome and resource intensive to deploy and operate. But regular LU&D
readers will understand that effective security is an involved process and won’t shy away from putting in the effort required to set up Qubes. Additionally, you can install the Whonix Template on Qubes OS – and you can always check our Qubes feature (see p60, Features, LU&D189) to get to grips with it.
Mayank Sharma