Meltdown and Spectre bugs hit millions of CPUs
Table of Contents

What is Meltdown and Spectre?
SOFTWARE BUGS ARE ten a penny, with devastating flaws found in applications all the time. This is one of the reasons that software is updated so frequently, patching security flaws to make things safer. Bugs in hardware are much rarer and much harder to fix, as we discovered recently when two massive bugs were confirmed to affect CPUs as old as from 1995.
Called Meltdown and Spectre, the two bugs represent a huge security threat to all computers. And because the problem is in hardware, the bugs affect all operating systems.
Meltdown was the first bug to be reported on 2nd January. It affects Intel processors, as well as newer Apple A-series chips and ARM chips using the R7, R8, A8,
A15, A17, A72 and A75 cores. AMD processors are immune to this attack. Spectre was revealed just a day later and is known to affect all processors.
Both bugs use similar design flaws in chips, allowing rogue processes to read protected memory in a system, pulling out sensitive data such as passwords. One rather scary video that surfaced online showed the power of Meltdown, with a password being stolen in real time as it was typed into a dialog box.
So what went wrong? The simple answer is that while chip makers managed to make their chips faster, they also made their chips less

secure. It all comes down to the way in which modern processors work, and how they try to be more efficient and maximise speed.
With modern operating systems, the idea is that, although there’s one pot of memory in a computer, all processes can share it securely. Operating systems and processes handle this through virtualization, creating pockets of data that only one application should be able to access.
The processor can read all memory and handles security by privilege, checking to see if a process is allowed to access the memory. In this way, a virus or rogue application shouldn’t be able to access data that belongs to another application.
The issue with Spectre and Meltdown comes down to a performance enhancement. Processors all have an instruction pipeline, which contains the list of jobs that have to be performed. Maximising pipeline efficiency and ensuring that it is never empty makes sure that the processor is never idle and that it operates in the most efficient way possible. Two of the ways in which the processor does this is with out-of-order execution and predictive execution.
With out-of-order execution, a processor re-orders instructions and runs them in a different, more efficient order. Provided that the result of the processing is the same, this makes no difference bar giving the CPU a performance boost.
Predictive execution lets the processor perform tasks ahead of time in the hope that they’re needed. They work by predicting the likely outcome of an instruction, then start work on the future instructions based on this, using a technique known as branch prediction.
This means that the CPU doesn’t have to wait for the result of one instruction before tackling the next one, which can give a huge speed boost. If the predictive instructions weren’t needed, the CPU resets back and starts over again.
The problem with both out-of-order and predictive execution is that instructions to access protected memory by a rogue process are handled before the privilege check has the chance to run. So a rogue process can ask for the contents of a bit of memory, and the CPU goes ahead and retrieves that information storing it in the cache. Only when the privilege check is run later does the processor then deny access to the data.
The rogue process can’t access the cached data, as it doesn’t have permission, but a clever technique, known as a cache timing attack, lets Spectre and Meltdown tell if a memory location is stored in cache. If that data is cached, the flaws know that it means that sensitive data is held, as it’s been recently processed by the CPU.

Another technique is then used to rebuild the memory location’s content. So even though a rogue process can’t physically access the protected memory, Spectre and Meltdown let the data be reconstructed and stolen.
The main difference between Spectre and Meltdown is how they work. Spectre manipulates a process into revealing its own data; Meltdown can access privileged data that the process would not normally be able to access.
The implications of these flaws are huge, as no computer is safe from the bugs, and all operating systems are affected.
SO WHAT?
AS THE EXPLOITS are hardware bugs with CPUs, there’s no way to fix the issue on-chip. Instead, operating system software patches have been released that mitigate the issues. Windows has been patched and your computer is safe as of 3rd January.
Meltdown required operating systems to change the way that the operating system’s kernel code worked. The kernel is the lowest level of the operating system, which can directly access hardware. By increasing the isolation between the kernel and user applications, it’s been possible to prevent Meltdown attacks from reading unauthorised memory.
Spectre can involve many different attack vectors, so trying to fix the issue will require many patches. Intel and AMD have both had to release microcode updates for their chips, in order to give software the controls they need to mitigate attacks. As exploitation via a JavaScript running in a browser is possible, Google has released an update to Chrome that specifically blocks Spectre attacks. You can expect to see further patches for other software in the future.
Google has created a new technique for dealing with the problem, called Reptoline. Software developers can use Reptoline for branch
Operating system software patches have been released that mitigate the issues. Windows has been patched and your computer is safe
prediction, which creates a safe predictive branch where no data can be stolen. This technique reduces the overhead, so should affect performance less.
The good news is that no attacks that use Meltdown or Spectre have been seen in the wild. The bad news is that dealing with hardware problems in software isn’t particularly efficient, and there’s a performance hit involved in fixing the issues. Of the two, it’s fixing Meltdown that has the biggest impact, meaning that Intel processors will be more affected than AMD ones.
Intel has revealed its internal benchmarks, showing the impact of Meltdown and Spectre patches. Tests were performed using 6th (Skylake), 7th (Kaby Lake) and 8th (Kaby Lake and Coffee Lake) generation processors, running on systems with an SSD. Gaming hasn’t been hit at all, with the GPU taking most of the strain, but productivity tasks were hit, and in some cases quite significantly.
Running the SYSmark 2014 SE responsive test, for example, the Skylake processor was 21% slower with the patch than without. PCMark 10 showed between a 3% and 4% drop across the entire processor range for the Essentials and Productivity tests. The WebXPRT 2015 benchmark, which tests web application performance, showed a drop of between 8% and 10% across the board for Windows 10.
AMD processors are immune to Meltdown and some variants of Spectre. There aren’t, at the time of writing, any benchmarks to show the impact of Spectre patches, but the impact of these flaws should be far less than with Intel systems.
Worse for AMD owners was the way that patching was handled, with the initial rollout putting some computers into endless reboot loops. Microsoft suspended the patches until a fix had been found.
Apple has released patches for macOS High Sierra, and there are patches for Linux operating systems, too. Meltdown and Spectre can also affect mobile processors. Apple has patched all devices running iOS 11 already, so you should update to the latest version to protect yourself. In practice, this means that all phones from the iPhone 5s upwards will get the required patches.
Android is more complicated, thanks to the broad range of manufacturers, each of which is responsible for releasing software updates. While Google has patched default Android, many older handsets won’t get the updates. Samsung, for example, has announced that the Galaxy S6 will get the update, but the Galaxy S5 will not.
For mobile handsets, the issues aren’t quite as bad as on desktop operating systems. With browser and software updates, many Spectre exploits will be blocked automatically. As mobile operating systems are more tightly locked down, it’s much harder for rogue code to get on your phone to run a Meltdown attack. As always, be careful what you install, and make sure that you only use well-known apps on the Google Play Store.
Unfortunately, the protections against Spectre and Meltdown are only workarounds. The only way to truly protect against both is with new processors, explicitly designed to eliminate these flaws. Intel has promised chips with built-in mitigations to these flaws later this year.
All we can hope is that this shock will make CPU companies take security more seriously and stop developing kit just for speed.
Spectre & Meltdown flaws hit CPUs hard
Intel, AMD and ARM processors are all affected in a various complex ways, causing panic, confusion and much hand-wringing by those in the industry.
By far the biggest tech story recently (sorry useless robots of CES 2018) has been the discovery of serious design-level chip flaws that can potentially be found in the majority of processors in use today. The flaws were first found by Google Project Zero researcher John Horn, and Werner Haas and Thomas Prescer from Cyberus Technology in Dresden. Germany, and Daniel Gruss, Moritz Lipp, Stefan Mangard and Michael Schwarz from Graz University of Technology based in Styria, Austria.
According to a timeline posted on The Verge (http://bit.ly/verge-spectre), Gruss, Lipp, Schwarz and Mangard discovered the fault late 2017, and on 3 December 2017 they had created a workable exploit for what would be called Meltdown, and contacted Intel. Apparently. Intel already knew about the issue, but asked the team to keep quiet. It wasn’t until the beginning of January 2018 that both the Spectre and Meltdown flaws were made public.
Meltdown (CVE-2017-5754) is a flaw that can be exploited to read the contents of private kernel memory by an unprivileged user, essentially enabling a program to access the memory of other programs and the operating system – something it wouldn’t usually have access to. Michael Schwarz tweeted a video of what an exploit for Meltdown could achieve.
The scale of the problem soon became apparent when it was revealed that all Intel CPUs with out-of-order execution since 1995 were potentially affected, apart from Intel Itanium microprocessors and pre- 2013 Atoms. No AMD CPUs are affected by Meltdown and only certain very new ARM processors are. For a list of at-risk ARM chips visit https://developer.arm.com/support/security-update.
According to Intel. Meltdown can be mitigated via operating system updates, and patches have already been released for Windows and Linux. Apple was hesitant to reveal that its devices were at risk (its own ARM processor are affected), but it released MacOS 10.13.2 and iOS 11.2. which contain mitigations. For more details on Meltdown you can read the whitepaper at https://meltdownattack.com/meltdown.pdf.
Meanwhile Spectre (CVE-2017-5753. CVE-2017-5715) can be exploited to gain

> Spectre and Meltdown flaws have been found in almost all processors manufactured during the past 20 years.
released that contain mitigations (because any attack using Spectre could likely use JavaScript).
More information can be found at https://spectreattack.com/spectre.pdf, but because Spectre and Meltdown are so widespread it’s likely your PC is vulnerable, so make sure your devices
Spectre and Meltdown are widespread so it’s likely your PC is vulnerable. Make sure your devices are patched and up to date
information from other running processes. This flaw is harder to exploit than Meltdown, but it’s also harder to mitigate and it affects AMD processors as well as CPUs by Intel and ARM. However, software patches for browsers and operating systems have been are patched and up to date, and that any patches you do install are from trusted sources. Malwarebytes discovered a fake Meltdown and Spectre patch that deposits ‘smoke loader’ malware on the victim’s Windows machine – read more at http://bit.ly/smoke-loaders.
Spectre & Meltdown: Linux devs respond
Linux machines are susceptible to the flaws in their processors, and distro makers were quick to issue patches.
The scale of the Spectre and Meltdown flaws are worrying, but the response by software developers has at least been reassuring. Systems running Linux are vulnerable to the flaws, but the community has been working hard to mitigate the issues, with numerous kernel updates being released. For people running Linux distributions using the standard kernel on x86 hardware, you should make sure you have an updated kernel. If you’re comfortable doing so, getting a release candidate (RC) update from the main kernel tree will enable you to have the most

> Android devices, such as the Pixel 2 XL, are susceptible to the flaws.
up-to-date patches (at the time of writing 4.15-rc9 is the most current release). If you’re sticking to stable kernels, make sure you have at least 4.14.15. If you’re using LTS kernels. 4.4.113+ and 4.9.78+ are the ones to make sure you have installed.
For ARM64 hardware. 4.16-rc1 is worth installing, and if you’re running Android, checkout the common Android Kernel tree at https://android.googlesource.com/kernel/common. These patches include mitigations for Meltdown.
Spectre is a bit trickier, but in the middle of January Kernel 4.15-rc8 was released, which included the Retpoline coding technique created by Google to mitigate against the flaw. According to Google on its Security blog (https://security.googleblog.com/2018/01/more-details-about-mitigations-for-cpu_4.html). Retpoline is a binary modification technique that protects against “branch target injection” attacks. More can be read about Retpoline at https://support.google.com/faqs/answer/7625886
Various distros have commented on the Spectre and Meltdown, as well as issuing their own mitigations, including Mint (http://bit.ly/mint-fix). Fedora (http://bit.ly/fedora-fix) and Ubuntu (http://bit.ly/ubuntu-fix)
Hardware makers react
Intel, AMD, Google and more attempt to repair the damage.
Despite Meltdown also affecting limited ARM chips, and Spectre affecting AMD and ARM as well, it was Intel that received the brunt of the bad publicity.
Intel initially claimed that any patches for the flaws wouldn’t introduce significant slowdowns on hardware, and by the middle of January it had released firmware updates for 90 per cent of processors made in the past five years. It also vowed to work with software developers and other hardware manufacturers to eliminate the flaws. However, this did not stop three class-action lawsuits being filed in California, Indiana and Oregon against the company (http://bit.ly/intel-lawsuits). with more expected.
Meanwhile, in a blog post (http://bit.ly/microsoft-reaction) Terry Myerson, Executive Vice President, Windows and Devices Group at Microsoft explained that patches for Windows machines for Meltdown and Spectre would have variable effects on the performance of those PCs. Some patches from Intel were also found to cause system instability in some cases.
It wasn’t plain sailing on AMD’s side, either, with the company slow to admit that its chips were susceptible to Spectre, with a class action lawsuit accusing the chip maker of keeping quiet about the problems. It also emerged that a Windows update meant to mitigate the issue was causing PCs running AMD chips to fail to boot (http://bit.ly/ amd-boot-failure). If you’re concerned about the hardware you’re running, check out the complete list of CPUs affected at www.techarp.com/guides/complete-meltdown-spectre-cpu-list
Microsoft disables Intel’s Spectre fix that ruins PCs
Microsoft has released an emergency security update for Windows 7, 8.1 and 10 to disable a fix from Intel that was causing computers to randomly restart and lose data.
Intel’s fix was for the Spectre processor flaw which – like the similar Meltdown bug – affects millions of devices worldwide, leaving them at risk of attack. Days after releasing the fix, Intel admitted it led to “data loss and corruption”.
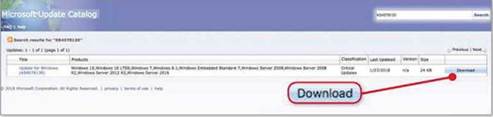
Intel urged users to ignore the fix and wait for the next one, but Microsoft plugged the gap by taking the rare decision to release an unscheduled (called “out-of-band”) update, numbered KB4078130. It’s designed to act only as an interim fix until Intel releases a more extensive update that doesn’t cause problems. Microsoft hasn’t installed
the update automatically on PCs because not all machines are suffering problems. Instead, you’ll need to install it yourself, but only if your computer has been rebooting unexpectedly or losing data since Intel’s Spectre update.
To do so, visit Microsoft’s Update Catalog (www.snipca.com/26941) then click the top-right Download button (see screenshot above).
Meltdown-immune processors
Intel didn’t comment on Microsoft’s update, but said it plans to release new processors “later this year” that will “directly address the Spectre and Meltdown threats in hardware”.
AMD, Intel’s biggest rival, said it plans to release new processors that will be immune to Spectre in 2019. Meltdown doesn’t affect AMD’s processors.
Both companies need to act fast because hackers are already exploiting the flaws. Researchers from German antivirus tester AV-TEST said that by the end of January they had identified 139 examples of malware that attempt to take advantage of them. However, they added there’s no evidence that attacks have taken place.
Meanwhile, four Republican members of the US House of Representatives have written to Amazon, AMD, Apple, Arm, Google, Intel and Microsoft, questioning whether it was appropriate to keep the flaws a secret for so long.
The companies agreed to secrecy in June 2017, hoping it would give them enough time to fix the flaw’s before they became public knowledge.
The firms planned to reveal the bugs on 9 January 2018, but were beaten to it by tech website The Register, who broke the story on 2 January. Google posted technical details of the flaw’s a day later. The letter argues that keeping the flaws secret left other companies vulnerable once they were out in the open.
Microsoft has confirmed that Office 2019 will only run on Windows 10 computers. The company explained its decision on its website (www. snipca.com/26942), saying that old software – including old versions of Windows – is difficult to keep safe, and lacks new features “to help people do their best work”.
The company also said it will end support for Office 2019 earlier than with previous versions, which were updated for 10 years. It will stop updating Office 2019 on 10 October 2025, which is also the same day it ends support for Office 2016.
A beta version of Office 2019 is expected in the spring, followed by a final release in the second half of the year.
We knew Meltdown and Spectre would be hard to fix, but we didn’t expect such a farcical series of events. As an illustration of the chaos unleashed by the flaws, you’d struggle to come up with anything better than Microsoft working overtime to elbow Intel’s fix out of the way. Thankfully for now, hackers have failed to develop malware that exploits the flaws, but that’s a timebomb which is ticking louder every day. We need more effective protection from all involved – Intel in particular.





