Tor Browser 12.0.3 Review
Nate Drake nosedives into the dark net with the Tor Browser and is blown away by its new censorship-resistant features. Read our Tor Browser 12.0.3 Review.
IN BRIEF
The Tor Project never fails to impress with its easy-to-set-up private browser, which doesn’t record a web history and hides your IP address. The latest version supports more languages than ever before and offers a selection of bridges to connect to Tor, even in countries where it’s censored.
specs
CPU: 1GHz
Mem: 512MB
HDD: 500MB
Builds: ARM64, x86_64
Since 2008, the Tor Browser has been making waves in providing online privacy. Successive versions are based on Firefox ESR (in this case version 102.8) and come with a number of features to make you as anonymous online as possible. Since our previous look in LXF263, the Tor Browser has seriously upped its game in terms of protecting your privacy and evading censorship.
Onion 101
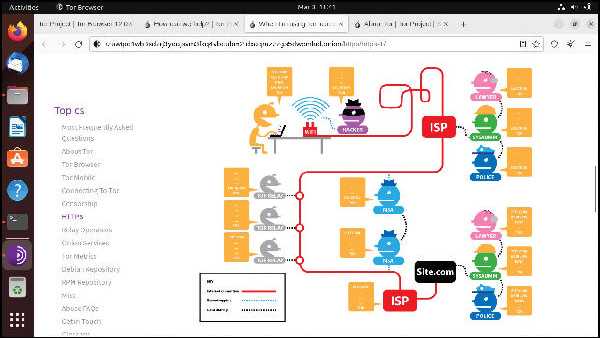
The Tor Browser uses so-called onion routing to keep your location and data safe. It works by encapsulating and removing various layers of the encryption, much like peeling an onion.
When the Tor Browser first launches, by default it searches for a list of Tor entry nodes, sometimes known as guard relays, and downloads the public encryption key for one at random. It then establishes an encrypted connection to this entry node.
The data packets sent to the entry node can then be encrypted and forwarded to a second Tor relay, using the second relay’s public key. The second relay has no record of the IP address you used to connect to the original entry node. It doesn’t even have any way to determine that the connection has come from an entry node.
Nevertheless, the second relay can establish a secure, encrypted connection to the original entry relay, allowing the Tor Browser to send data packets to a third relay, which only it can decrypt. This is the nature of a Tor circuit – a path through the Tor network where each successive relay can only forward data packets and decrypt only those encrypted with its own public key.
When the circuit is complete, you can browse the web anonymously. Volunteers run exit nodes, which are capable of connecting to the regular, clear internet, which can then be passed back to you along the circuit you’ve established. In this case, the successive layers of encryption are removed from data packets.

The Tor Browser protects your privacy by routing your data packets through multiple relays.
Use virtual bridges to connect to Tor in countries that try to restrict the network.
The bottom line is that as data packets move from one Tor node or relay to the next, no single node knows both the origin and final destination of that data.
Hidden services
Although the Tor Browser can access the regular internet, it’s difficult to trust complete strangers who run the exit relays. Any unencrypted information you access on the web via the Tor Browser can, in theory, be harvested or manipulated by bad actors.
Luckily, there’s an alternative. Tor hidden services are websites that can only be accessed via the Tor network (usually via the Tor Browser). Their addresses reflect the public key of the service in question, so usually resemble gibberish. They use the TLD .onion; the New York Times, for instance, can be found via https://nyti.ms/41Muny4/.
Each time you connect to a Tor hidden service, your connection is still routed across multiple, encrypted hops, but your traffic never leaves the Tor network. This is much more secure than using an exit relay, provided your chosen website has a .onion address.
Since our last look at the Tor Browser, the first time you visit a website for which there is a Tor hidden service, the browser now asks if you want to prioritise .onion addresses over clear net ones. That means if you go to a regular website, such as that for the Tor Project (https://www.torproject.org) itself, in the Tor Browser, you’re automatically redirected to its .onion address.
Burning bridges
If you’re reading this article and are new to Tor, you’ve probably noticed a major flaw in onion routing: it requires you to establish a connection to an entry relay before you can establish a Tor circuit.
These entry relays are listed in a public directory, so can be targeted by bad actors. The Great Firewall of China for instance, often blocks entry relays using DPI (deep packet inspection) and impersonating other nodes.
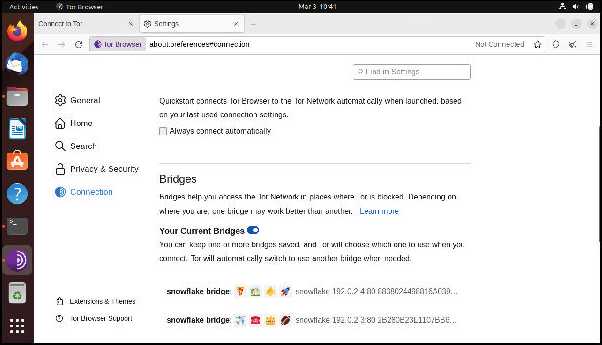
In theory, you can get around this restriction using a bridge. These are slightly-modified Tor relays operated by Tor volunteers that aren’t publicly listed. That means that there’s no immediate way to detect and block them, because the IP address isn’t publicly available.
Traditionally, users have connected to bridges either through using the small number of addresses built into the Tor Browser Bundle or by requesting them from https://bridges.torproject.org.
Unfortunately there’s nothing to stop bad actors in oppressive regimes from doing the same and blacklisting their IP addresses, which is why the Tor Browser now has new bridge bolt-ons for those people living under censorship /see boxout).
Footprints and fingerprints
The Tor Browser is set never to store your browsing history. This means each time you close it, all cookies and other browsing data vanishes. You can save bookmarks, though. You can also download files, but the Tor Project advises against it, as it makes you easier to profile.
There’s also a button on the browser bar you can click to immediately close all windows and establish a new Tor circuit, effectively creating a new identity.
While we’re on the subject, the Tor Browser is highly resistant to fingerprinting. When you visit a website, your browser supplies a user agent string indicating browser type, your language, certain device settings and so on.
This combination can be used to identify you, which is why the Tor Project’s ethos is that everyone using the browser should have the same fingerprint. This is also why the developers strongly advise against adding any other of your favourite plugins or themes to the Tor Browser post-install.
The latest version of the browser actually only comes with one plugin: NoScript, which, in fairness, should stop malicious code dead in its tracks. Previously the Tor Browser included HTTPS Everywhere but this is no longer necessary as Firefox can force https-only mode.
Multi-locale
If English isn’t your first language, previous versions of the Tor Browser required you to visit the Project website and download an additional language pack. The latest version of the browser now comes with all supported languages bundled.
This means that on first install it matches itself to the system language. You can also change the language from the browser settings without downloading more files. This latest stable release is also the first to support Albanian and Ukrainian.
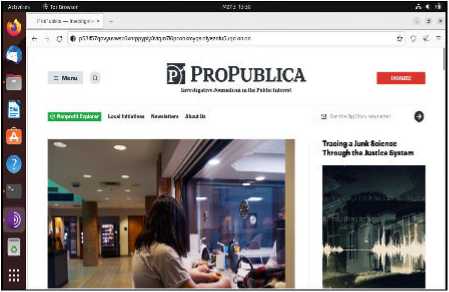
Tor Browser can now default to the .onion address for clear net websites.
Tor torments
If you’ve never used the Tor Browser before, you need to prepare for the fact that routing your data packets through multiple relays is a slow process. If you remember the heady days of dial-up internet, you’ll have some frame of reference. This makes the browser unsuitable for downloading large files, using with P2P software or streaming video.
There’s a built-in onboarding tour on the homepage, which lists some of the key features. There’s also a built-in user manual.
Tor data packets are also very distinctive and are sometimes blocked by ISPs who are convinced that the browser is only used for illegal purposes. You may be able to circumvent this, however, using an obfs4 bridge /see boxout).
VERDICT
DEVELOPER: Tor Project WEB: www.torproject.org LICENCE: 3-clause BSD
The Tor Browser is great for concealing your location, as long as you can live with limited features and slow browsing.
» Rating 7/10
______________________________________________________________________________
» BUILDING BRIDGES
The latest version of the Tor Browser is more censorship-resistant than ever before. Just click Configure Connection on first launch, then scroll down to Bridges and choose Select A Built-In Bridge.
As you’ll see, there are three principle types of bridges (sometimes known as pluggable transports). The obfs4 bridges make your traffic look like random noise, whereas meek-azure makes it seem as though you’re connected to Microsoft’s Azure servers. The traffic is encrypted in each case. This can be useful if you’ve already established a Tor Circuit.
Snowflake bridges are maintained by kind volunteers who install a special Firefox, Chrome or Edge browser extension, giving a little of their bandwidth towards helping people in oppressive regimes to connect to Tor. As installing a plugin is much more convenient than running a bridge, the sheer number of Snowflake bridges is (in theory) far too great and changeable to censor effectively.
Snowflake traffic also attempts to disguise itself as web traffic, but various Reddit users have reported that the Chinese government has had some success in blocking Snowflake bridges. It also works via WebRTC which can (in some cases) compromise your privacy. (View a full technical rundown at https://bit.ly/LXF301snowflake/.)
If you’re still having trouble getting online, choose Request A Bridge and complete the captcha to obtain a new address. We noted in our tests, though, that the browser kept saying the captcha was entered incorrectly. You can also request new bridge addresses from https://bridges.torproject.org/options/.