STOP WI-FI HACKERS

There’s something rather magical about products that ‘just work’. Smart TVs, speakers with built-in voice assistants and video doorbells all fall into this category. Plug them in, connect them to your Wi-Fi, and you’re ready to go. There’s very little to configure and usually even less to maintain. Read our STOP WI-FI HACKERS.

The trouble is that such convenience can provide a false sense of security – and that can lead to complacency. Smart devices – just like computers – are often eminently hackable and you’re reliant on the manufacturer to remotely apply the necessary security patches and updates in a timely manner. If they don’t, you risk hosting an unsafe device on your network, which could put other devices, including your PC, at risk.
If you don’t believe us, read around. There have recently been reports of vulnerabilities in outdated Google doorbells (www.snipca.com/47425), and claims that devices from rival Ring have been accessed by hackers (www.snipca.com/47427). Researchers in Texas found a way to issue silent voice commands to smart-home devices (www.snipca.com/47428), while UK and Italian researchers managed to extract Wi-Fi passwords with the help of a smart light bulb (www.snipca.com/47429).
This means that if you’re running any internet-connected ‘smart’ device in your home, it’s essential to strengthen your defences, both through the device where possible, and on the network itself. Here we explain the most reliable ways to make your Wi-Fi unhackable.
YOUR SMART HOME SECURITY QUESTIONS ANSWERED
Why would anyone want to hack a smart device?
Some hackers break into devices purely for the fun of it or to prove they can do it. Similar to trainspotters collecting locomotive numbers, they want to add more and more conquests to their list. However, they’re not the ones you need to worry about.
A determined intruder usually has more malicious aims. To them, an insecure device is an entry ramp to your network. Many smart-home devices run sophisticated operating systems – often a version of Linux – designed to perform a specific range of functions. They may also contain a small amount of unused onboard storage.
When a hacker detects a vulnerable device, they can use that storage and the operating system’s dormant features to execute their own code. And, because the same smart devices are in millions of homes worldwide, the hacker can apply what they’ve learned about the vulnerabilities of one device to any other they come across, quickly building up a network of compromised gadgets under their control.
How do hackers find an insecure device?
Think of your router as a block of flats with a purely numerical street address (technically known as its IP address). The building contains several ports – front doors in our analogy – behind which live your devices, and through which they send and receive data.
In much the same way as real-world burglars might drive by your home, hackers can trawl the internet using IP-address scanners (as pictured above right). When they find an address hosting a network, they work their way through every port until they find one that’s open. If a vulnerable smart device lives behind that port, they’ll be able to repeat a hacking routine they’ve performed many times elsewhere to infiltrate your gadget and reprogram it to do whatever they choose.
While it may appear to be functioning normally, your compromised smart device could then start sending the hacker your passwords and payment-card details; help compile a pattern of movements that indicate when your home is unoccupied; or attack other devices on your network.

So as long as my router is secure, aren’t I protected?
Keeping your router’s firmware updated helps, but it’s not the only thing you need to worry about. Smart devices spend all day communicating with remote servers through authorised ports. Unless your router is inspecting the data that’s passing through it, working out where it’s heading and whether that’s what you intended (which would be a huge and impractical task) it’s got no way of knowing that it’s acting as a conduit for stolen data.
Does my risk increase with the number of devices?
Not necessarily. You could add 1,000 video doorbells, internet-connected printers or TV streaming sticks to your network and – if they all come from reputable brands – you’re very unlikely to introduce a vulnerability. Or, you could add a single Wi-Fi camera from an unknown manufacturer (like the one pictured below), or a second-hand device that’s been maliciously reprogrammed, and your network will be exploited within an hour.

What kind of devices should I be worried about?
Anything that has access to the internet. However, while it’s a good idea to be cautious when adding any device to your network, you should be more wary of less familiar brands. If a device from a big-name brand was ever found to be insecure, it would be headline news, could damage the company’s sales and tarnish its reputation beyond repair. In short, big brands have more to lose.
Considering the cost of developing, manufacturing and marketing a smart product that nobody else sells, that’s something they’d try to avoid by making sure their devices are as secure as possible, and that they stay that way through frequent updates.
Do smart devices get less secure as they age?
That can happen. Security measures in the past were certainly less foolproof. A few years ago, we might have suggested swapping letters for numbers to beef up your password security – so, ‘pa55w0rd’ rather than ‘password’. Bots got wise to that trick, so we advised throwing in capital letters, then a few years later, adding special characters and punctuation.
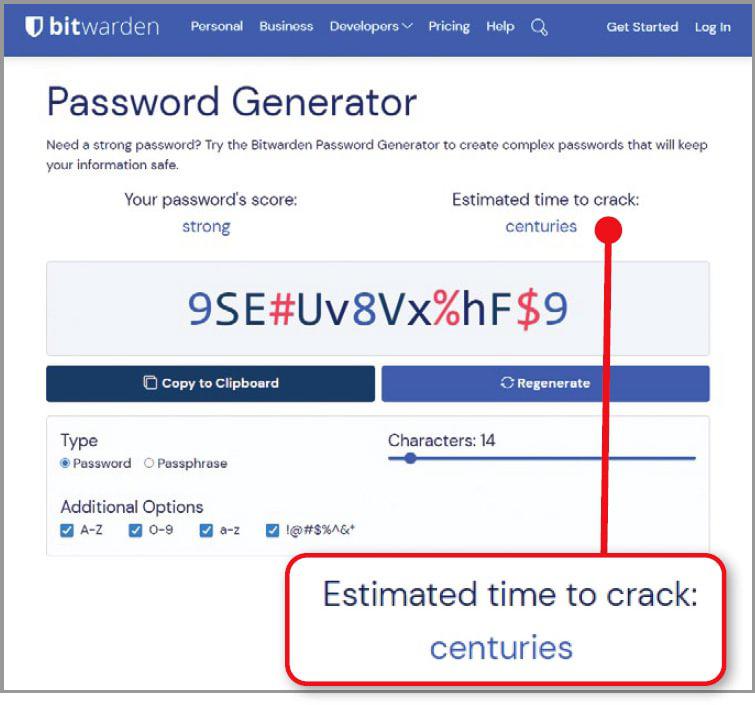
Today, we recommend using a password manager such as Bitwarden (www.snipca.com/47395) to generate strong passwords (see screenshot on page 52), though many security experts believe it’s time to move beyond passwords altogether.
Network security standards have also changed. WEP (Wired Equivalent Privacy), introduced in 1997, was once considered state of the art when it came to securing a wireless network. Then, in 2005, the FBI demonstrated that it could be cracked in less than three minutes using publicly available tools.
WEP was replaced by WPA (Wi-Fi Protected Access), and WPA by WPA2, then WPA3. So, if your smart device is still using outdated security protocols, it will be less secure today than it was when you bought it because it hasn’t kept up with these technological advances.
So, do I need to update my smart devices’ software?
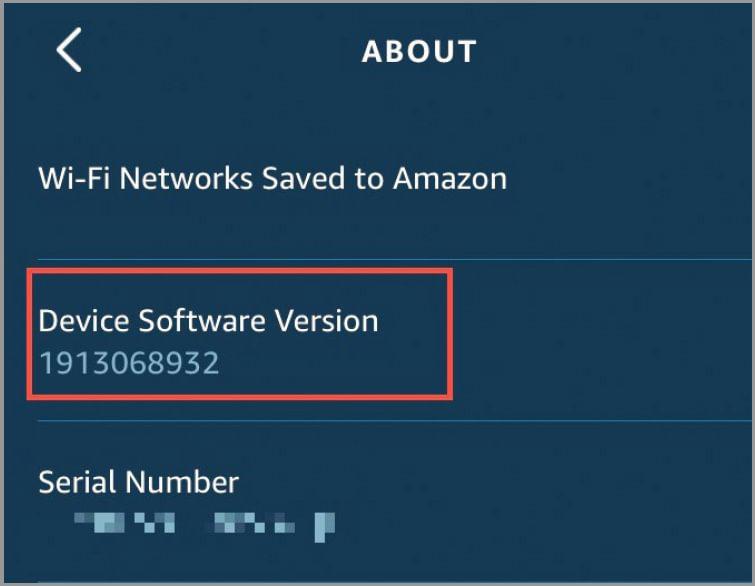
If you can, you should (see page 56), although it’s not always necessary. For example, many smart devices, including Amazon’s Echo speakers and Fire TV Sticks, update themselves automatically. If you have an Echo speaker, you can check that you’re using the most recent firmware in the Alexa app. Tap Devices on the toolbar, followed by ‘Echo & Alexa’, then the device you want to check. Tap Status, then scroll to the bottom of the screen and tap About. Compare the number below Device Software Version (see screenshot above right) against the list at www.snipca.com/47329.
If you have a Fire TV device, use your remote control to select Settings, then My Fire TV. Click ‘About’, then check the number below Software Version and compare it to the latest release for your device at www.snipca.com/47328.
Neither Fire TV nor Echo speakers need a web interface, but other smart devices do so you may be able to update your device from there. The steps you need to take will depend on the device. Start by logging in using the device’s address on your network, and the administrator username and password. If you haven’t changed these, they’ll often be shown on a sticker on the device itself. Click through the dashboard until you find an option to update the software, then check the manufacturer’s website for the latest release. Make sure you keep the device connected to your network and the mains throughout, as a failed update can make the device unusable.
Wi-Fi SECURITY SETTINGS YOU MUST CHANGE
Change your default passwords
Almost every Wi-Fi router comes with a default username and password. Recently, manufacturers have become better at setting these as random words or strings of letters rather than the much less secure ‘admin’ and ‘password’ of old. As we mention in the box opposite, you can find details for most routers at www.routerpasswords.com (see screenshot below).
However, it still makes sense to reset any default to something different to prevent hackers from being able to access your network through your router’s settings.
You can change your router’s administrator password through its browser-based control panel. Note that this is the password used to access the control panel itself, and not to log on to your Wi-Fi. If you want to change the Wi-Fi password as well, this is also done via the control panel, but will need to be managed separately.
If you’re changing the administrator login password, consider writing it on a label and sticking it to the router itself. While we would not usually recommend writing down a password, it is common practice for routers to have their login passwords attached to them when they come from the factory, so this is only sticking with convention.
Few smart devices have passwords that you need to type in yourself. They are usually managed using apps on your mobile phone and, as long as nobody else has your phone, that should keep them safely out of reach.
However, some log into online accounts to perform specific functions, such as Wi-Fi-enabled thermostats that manage your boiler, or security cameras that upload footage to online storage. You will usually be prompted to provide your own password when setting up these kinds of online accounts rather than being given a default password.
It still makes sense to change the password every so often, though – particularly if news breaks of a data breach or leak from the service in question. The exact process for doing this varies by product, but start by checking any associated app and, if that doesn’t include a relevant option, try logging into the service through your browser.
Turn on your router’s firewall
Turning on your router’s built-in firewall lets you block internet traffic, whether incoming or outgoing, through specific ports – or entirely. By limiting the number of routes through which data can travel, you also limit the number of opportunities hackers and compromised smart devices have for accessing and transmitting your personal information.
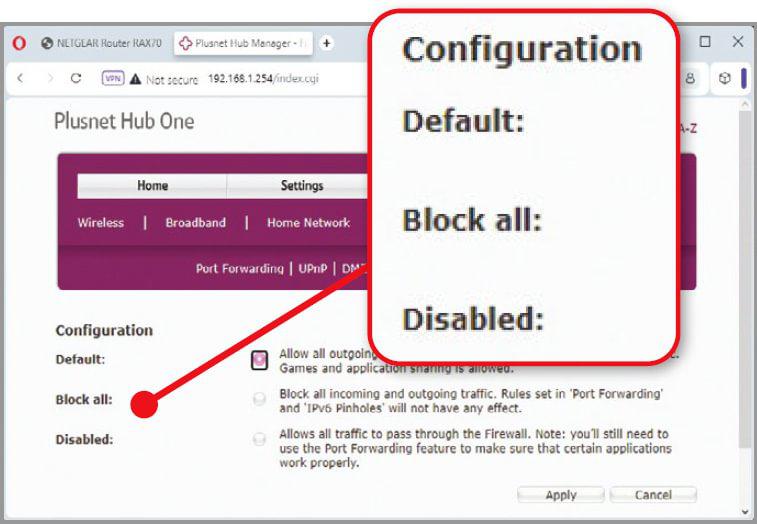
You may have come across the Windows Firewall – most likely when it popped up an alert and asked you to authorise (or deny) a particular action, but the firewall built into your router won’t display these alerts because it will make those decisions based on rules you set.
At its most basic, your router’s firewall will have options like the three in our screenshot above, where the default is to block all unsolicited incoming traffic, but allow outbound traffic. However, other options on this router also allow us to authorise specific traffic types, such as data for bespoke games, mail servers and video-chat services. In most cases you won’t need to make any such adjustments, which makes enabling the firewall as close to a one-click security measure as it’s possible to get.
Update your Wi-Fi encryption
You should always use the most recent encryption supported by your router. Ideally, this will be WPA3, but as this is relatively new your router might not support it – especially if it’s an Internet Service Provider (ISP)-supplied device you received on signing up 10 years ago.
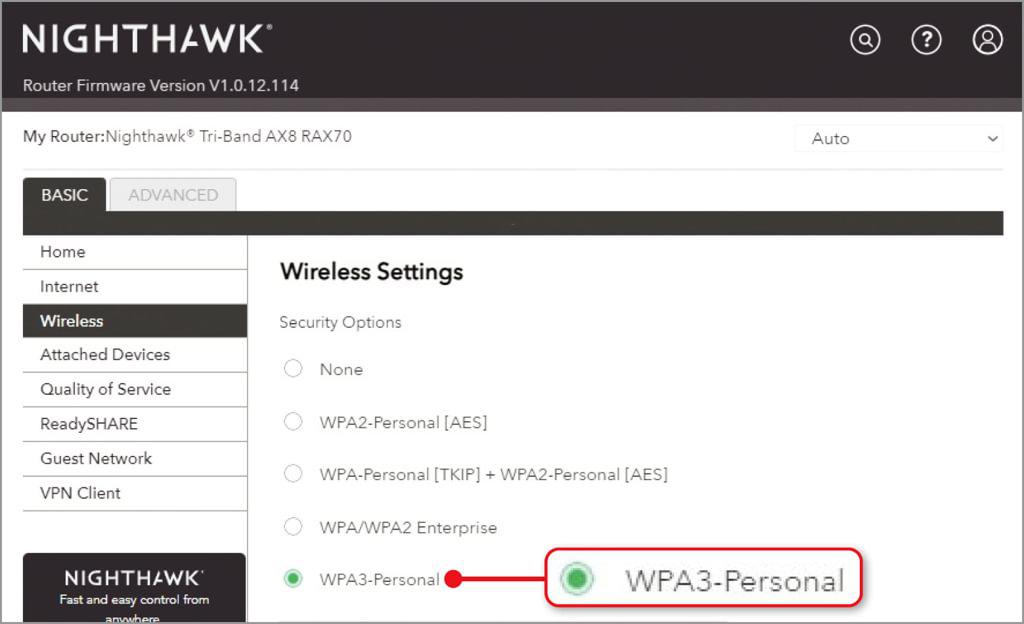
If your router doesn’t support WPA3, opt for WPA2 Personal if your router offers that, or WPA2-AES as a stopgap, but bear in mind that because this encryption technology has been previously compromised, it doesn’t give you complete protection.
There are two different kinds of WPA3 encryption – Personal and Enterprise. As its name suggests, Personal is the best for home use, so if your router offers both options, choose this one (see screenshot below).

Ditch your ISP router
If your ISP-provided modem-router doesn’t support WPA3, we’d advise buying a new router to boost your security. You can buy a WPA3 router with the latest security protocols for around £ such as this TP-Link model from Amazon (www.snipca.com/47403, pictured above), which should help keep your network and devices safe.
It’s unlikely your ISP will agree to send you a new router for free if your existing modem-router combo still works. So, if you do buy a new WPA3 router, connect this to your ISP device using one of its Ethernet ports. Next, turn off the wireless networking features of your ISP’s device so it’s just acting as a modem, and use the new router to broadcast a better protected wireless network around your home.
BLOCK INTRUDERS FROM YOUR Wi-Fi
Keep your neighbours off your Wi-Fi
Wireless networks are usually set to broadcast their name so they’re easy to find and connect to. This name is known as the SSID – or Service Set Identifier – and it’s what you click when you choose a specific network from the Windows taskbar or in the list of networks on your phone or tablet.
However, this convenience is only a good thing if you also use a strong password. If you use something that’s easy to guess, like the name of a pet, anyone who knows a little about you and lives within range of your signal could easily find their way on to your network. Once there, they could exceed any cap you have on your broadband data allowance, or connect insecure devices over which you have no control. All of which would undo the good work you’ve done in securing your network and devices.
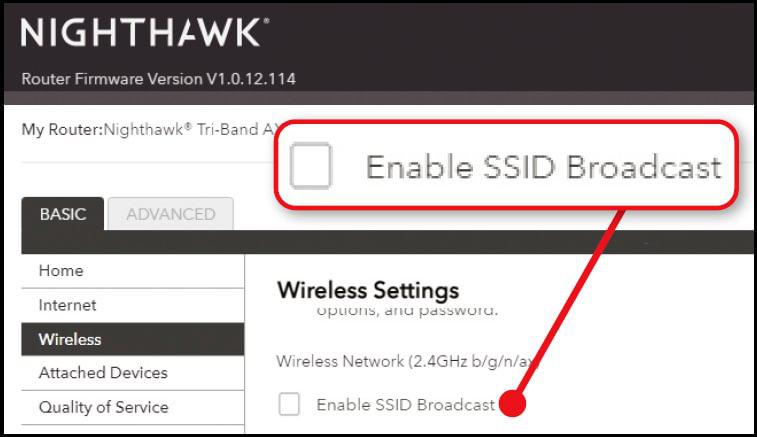
If you suspect your neighbour is piggybacking your network, first hide your SSID by turning off the option to ‘broadcast’ this in the router’s browserbased control panel (see screenshot below).
Now, change the SSID to something you’ve not used before, and choose a new password. As the SSID is now hidden, anyone who wants to connect will need to already know both the network name and your password, which effectively doubles your security.
It therefore makes sense to choose something quite complex for the network name. Ideally, it shouldn’t be difficult for you to remember, but it should be very tricky for someone to guess.
You’ll now need to reconnect your devices to your network, as they no longer recognise its name and can’t see the SSID. To connect a Windows 11 computer, click the Wi-Fi symbol on the taskbar, then the right half of the split Wi-Fi button. Click ‘Hidden network’ in the list of networks, then enter the SSID and password. If you’re using Windows 10, click the Wi-Fi icon on the taskbar, followed by Hidden Network. To reconnect your smart devices, use their associated apps on your phone.
Block unauthorised devices on your network
Routers need to keep track of the devices – technically known as ‘clients’ – that connect to them, so they know where to direct the data they receive. As such, they can draw up a list of connections you can scan for any unfamiliar entries. After logging into your router’s control panel, look for an option for DHCP client list, attached devices or similar.
It’s often possible to temporarily block a device from the client list, so, if you spot something suspicious, block it, then make sure all of your computers, and smart devices – such as video doorbells, speakers and streaming sticks – still work. If something no longer functions as expected, it’s probably the device you blocked, so unblock it.
To ban devices on a more permanent basis, it’s usually possible to block their MAC (Media Access Control) address, rather than their IP address (see box, right). The MAC address is a unique string of letters and numbers, organised in pairs, that’s used to identify the networking circuitry inside the device. So, while your computer will technically have a MAC address, it’s not assigned to your computer so much as it is to its network card.
Click a client in the list of attached devices to see whether your router reveals more details. If it does, and these details include the MAC address, select and copy it. Next, look for an access control option and, if this reproduces the list of clients you were just looking at, use the tick boxes that it displays to block the unauthorised device. If you need to manually enter the MAC address of a device you want to block, paste in the address you just copied.
Hide your entire network behind a VPN
One of the most effective ways to secure the data your PC sends over the internet is to use a VPN. Any VPN tool running on your computer encrypts the data before transmitting it, and doesn’t decrypt it until it reaches its destination. That way, if anything or anyone is snooping on your connection, all they will see is scrambled gobbledegook.
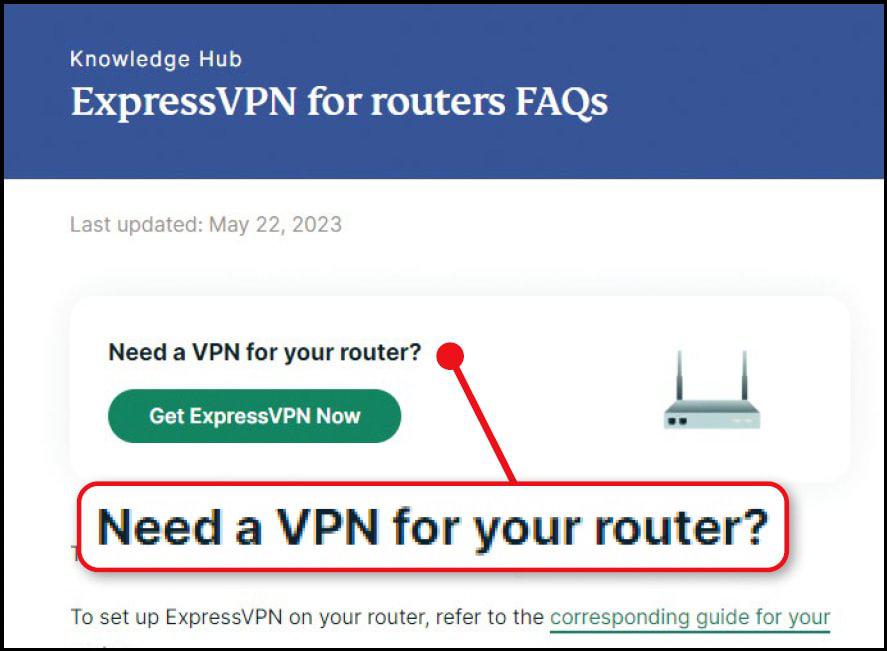
You can also run a VPN on your tablet or phone but – because you’re not usually able to install software on them – you won’t be able to use a VPN on a smart device such as a speaker with a built-in voice assistant, a video doorbell or a smart camera.
Depending on your router, you may be able to get around this limitation by signing up with a VPN provider and entering your login credentials through the router itself. This allows the router to encrypt all of your internet traffic, whichever device it originates from and saves you having to install VPN software on every PC, tablet or phone on your network.
Most of the best paid-for VPNs can be installed on your router, including ExpressVPN (www.snipca.com/47418, pictured below left) and NordVPN (www.snipca.com/47419). Free VPNs, which have limited bandwidth, don’t generally offer this option.
If you do go down this route, obviously remember that when you’re not online via your home network, your traffic won’t be processed by the VPN, so it won’t be encrypted. This is something to bear in mind if you use your tablet or phone during your commute, or connect to a coffee shop’s Wi-Fi from your laptop.
Schedule your Wi-Fi to disconnect at night
As well as hiding your router’s SSID and changing your Wi-Fi password, you can switch off your network when it’s not needed. That way, any devices connected to it will be immediately disconnected, and they’ll be safely out of the reach of hackers. Plus, your neighbours won’t be able to piggyback your connection while you’re asleep.
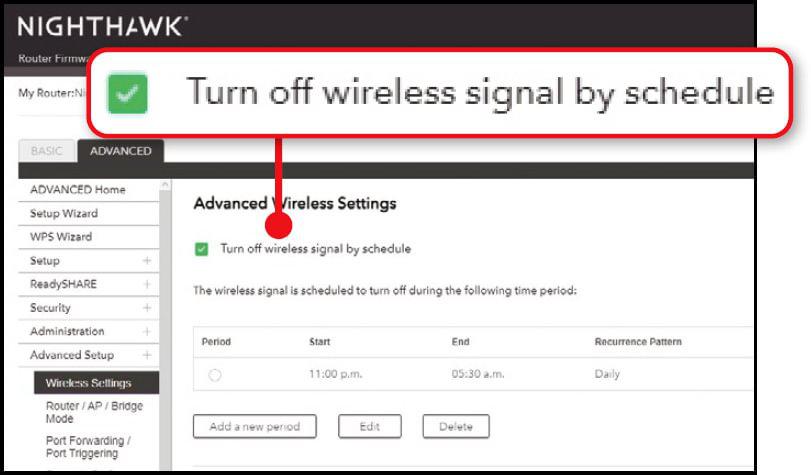
There are several ways to do this. Two physical options are to switch off the router at the wall, or use a timer plug. However, we wouldn’t recommend regularly disconnecting your broadband. That’s because internet providers monitor the connections between customers and their servers, and use a technology called Dynamic Line Management – or DLM – to tweak each line’s individual settings to maintain a stable connection. If you regularly turn off the router, DLM might interpret this as instability on the line and reduce the speed of your connection in an effort to improve overall performance.
Turning off just the Wi-Fi while leaving the router on and connected gets around this problem while still allowing you to shut down the network at night. If your router supports this scheduling option, you’ll find it in the browser-based control panel (see screenshot above).
Be aware that some smart devices may try and call home in the small hours for software updates, which they won’t be able to do if they don’t have a physical connection to your router (which will still work even when Wi-Fi is turned off).
SECURE YOUR SMART DEVICES
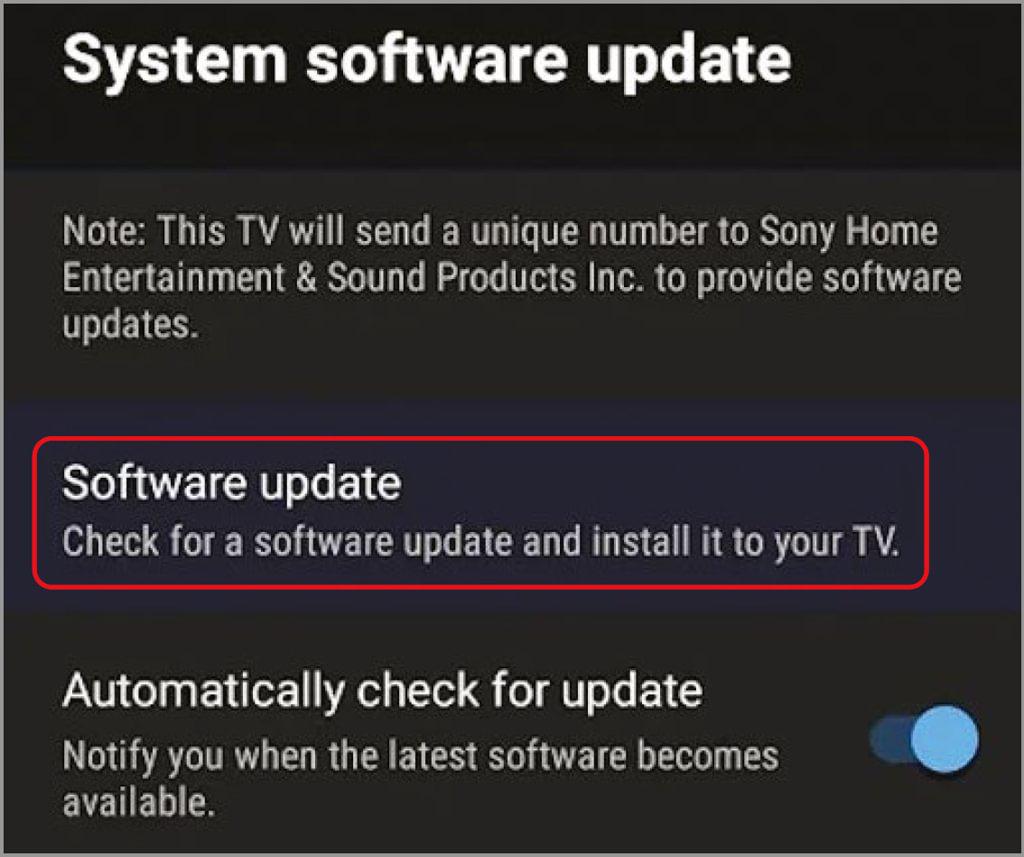
Update your smart devices’ software
Smart TVs and voice assistants have operating systems that let you interact with them directly. Other smart devices, including plugs, Wi-Fi-connected light bulbs and security cameras, have what’s known as firmware. This is software you can’t interact with directly, but which is used to manage and provide their core services and functions.
Manufacturers update both operating systems and firmware over time and when vulnerabilities come to light, so it’s important to ensure you’re always running the most recent release on every device.
In many cases, they will update themselves – often overnight when not in use – so all you need to do is check that they’re up to date. You usually can do this on your smart TV by going into the About section of its settings and selecting ‘Software update’ or similar (see screenshot below). For devices without a screen, you can update the software through the associated app.
If there’s no way to manually update a device and it’s not running the latest software, check with the manufacturer as to why this might be. If they’ve stopped supporting a device, it’s time to think about replacing it, because running outdated firmware on one device can put other devices on your network at risk.
Isolate smart devices on a guest network
From smart TVs and speakers to laptops and desktop PCs, you probably have lots of devices on your network and, if just one of them is vulnerable to attack, it could provide a point of entry for hackers who want to steal data from your PC, or encrypt it and demand a ransom to unlock it.
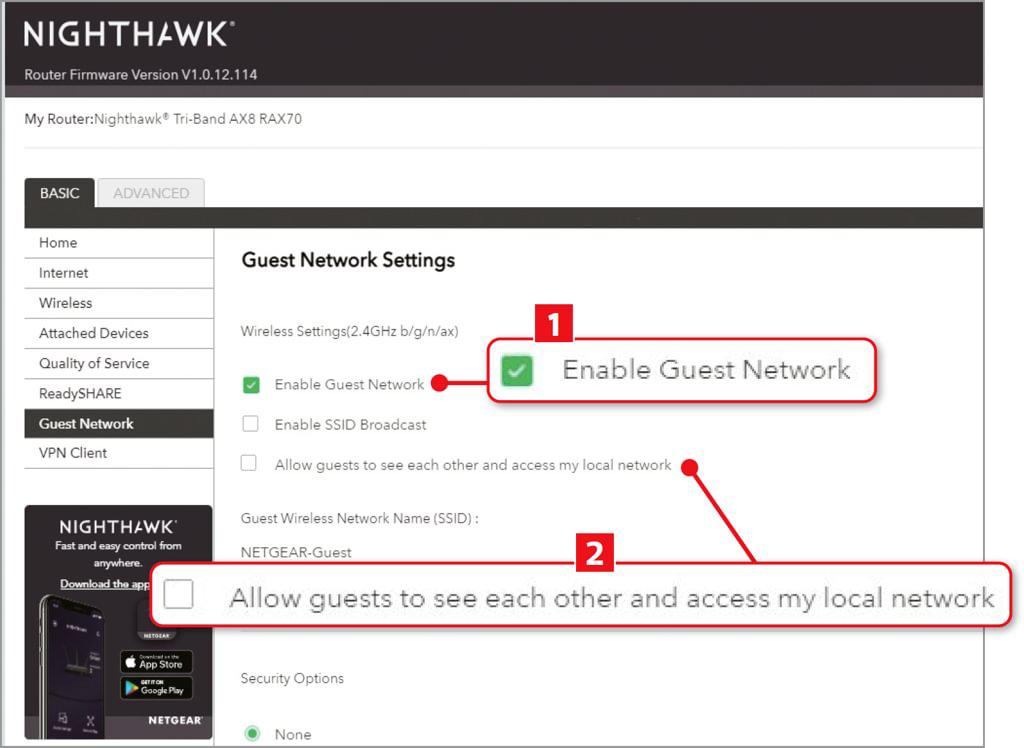
One of the most effective ways to mitigate this is to keep all your smart devices on a separate network from your main computer. That way, if one of them is compromised, your PC should remain out of reach.
In most cases, you won’t need to set up a second router to host a separate network, as most routers – even those supplied by ISPs – let you set up what’s known as a guest network. While this has access to the internet, just like your regular network, it’s isolated from your primary network.
Enabling a guest network is usually a one-click operation in the router’s browser-based control panel (1 in our screenshot above). If you also have an option to allow guests to access your local network, make sure this is disabled 2.
Stop snoopers watching your CCTV
Security cameras can be the most revealing of all smart devices if a hacker gains access to them. Not only could the hacker be watching you going about your daily business, but they could also build up a detailed record of your movements, so they know when the house is likely to be empty.
The usual advice about changing any default passwords naturally applies here, but if you also have the option of applying two-factor authentication (2FA) you should enable it. 2FA keeps a record of authorised devices and, when an unfamiliar device tries to connect, it requests a code, either from a pre-authorised authenticator app, or by sending the code via a text message to a pre-registered phone number for you to type in.
If the hacker doesn’t have access to your authenticator app and they have no way of accessing your messages, this will go a long way towards keeping their eyes off your camera feed.
Secure your smart doorbell data
Uploading videos from your smart doorbell to online storage is convenient, but it costs money and sends the data outside your home, which is an obvious security risk. If you prefer to keep the data local, choose a system that comes with its own storage.

Amazon’s Blink Video Doorbell (www.snipca.com/47400) and Blink cameras can save data to the company’s Blink Add-On Sync Module 2 (www.snipca.com/47401, pictured above), which costs £ when bought on its own but is bundled with some multi-camera packs.
This module has a USB port to which you can attach a USB stick. We’re using a Sandisk Ultra Fit drive (www.snipca.com/47402) with ours because it’s about the size of a thumbnail, so doesn’t protrude far when plugged in.
The bonus of saving video locally is not only that it doesn’t leave our home, but we also don’t need to pay an ongoing subscription for cloud storage.
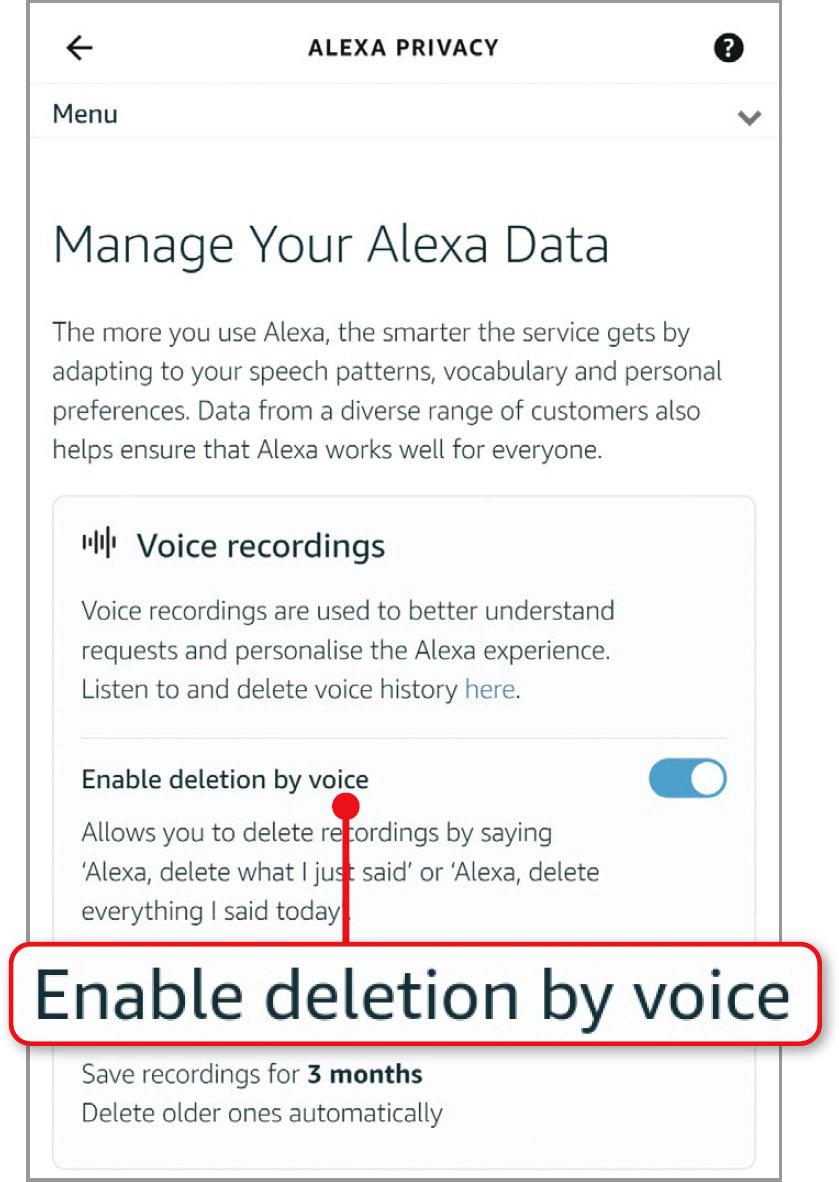
Stop your smart speaker saving your voice
Smart speakers are listening all the time. If they weren’t, they wouldn’t be able to detect their ‘wake word’. However, you can check what your speaker has heard, and limit what it records.
If you have an Echo device, open the Alexa app on your phone and tap More followed by Settings. Select ‘Alexa Privacy’, then Review Voice History. By default, the app will show you all the audio captured over the previous 24 hours, but you can change this by tapping Displaying, then choosing options from the ‘Filter by date’ and ‘Filter by device or profile’ menus.
If you only want to delete one or two specific recordings, select them in the list and tap the ‘Delete recording’ button. If you want to delete everything, select All History in the ‘Filter by date’ menu, then tap ‘Delete all of my recordings’.
To save time, you can enable this feature by voice. Return to the Alexa Privacy screen and tap Manage Your Alexa Data. Switch on ‘Enable deletion by voice’ (see screenshot right) and you can use commands such as: ‘Alexa, delete everything I said today’.
You can also decide how long Alexa should keep recordings. Tap ‘Choose how long to save recordings’ and select one of the options, which range from keeping them until you manually delete them to not saving recordings at all.
If you have a smart speaker with Google Assistant built in, voice-activated deletion is already enabled. Say “Hey, Google, delete today’s activity” to delete what you’ve said in the last 24 hours. Change this to ‘this week’s activity’ to wipe the previous seven days.
You can also browse and delete your recordings by visiting the Google Assistant activity page in your browser (www.snipca.com/47399).
WHAT YOU CAN DO
• Change the default password for accessing your router
• Upgrade your encryption to the highest level
• Stop your neighbours stealing your Wi-Fi
• Identify and block unauthorised devices
• Schedule your Wi-Fi to disconnect at night
• Update the software on your smart devices
• Isolate your PC from other Wi-Fi devices





