Securing wireless
[ HOME NETWORKING ]
Securing wireless
ATHREE STEP GUIDE TO MAKING WI-FI SAFE.
[ NATHAN TAYLOR ]
IT TOOK TIME, but most wireless solutions now ship with security on by default. Gone are the days of default open wireless networks or the use of insecure WEP (wired-equivalent privacy). It’s much harder for hackers to access wireless networks now – but it’s still not perfect.
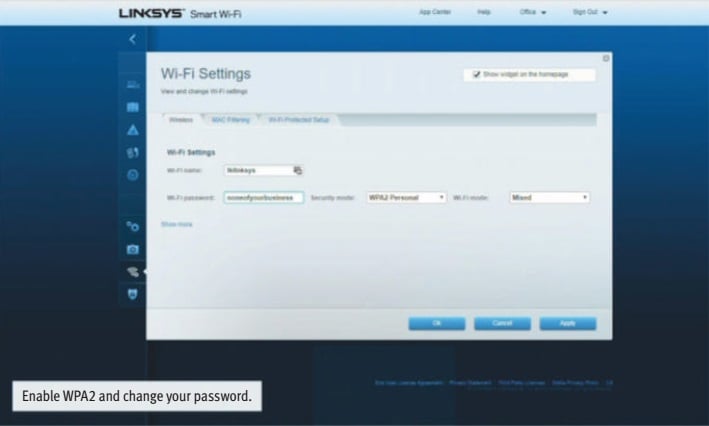
Table of Contents
To ensure that your wireless usage is secure as possible, there are still three things you should do. This month, we’re going to walk you through them.
ENABLE WI-FI PROTECT ACCESS 2 (WPA2) – WITH A GOOD, PERSONAL PASSWORD
The first thing you should do on any new or old router or access point is to ensure that WPA2 is enabled. The vast majority of new devices sold now do indeed have it switched on by default as well as a unique password in the box or on a sticker attached to the device. But it’s worth checking and making sure that WPA2 is indeed switched on, as well as customising your password.
To do this, you’ll have to log on to your router’s admin console or mobile app. Find the settings for Wi-Fi security. Ensure that WPA2 Personal/Pre-shared key is enabled, and type in your own password. As with all good passwords, it should include both numbers and letters, upper case and lower case as well as symbols. Dictionary attacks (where the password is tested against a dictionary of common words and passwords) are possible on Wi-Fi, so your password should not be a dictionary word or something easily guessed.
WHY THIS IS IMPORTANT
The reason we use WPA/WPA2 is because the older system WEP (wired-equivalent privacy) proved to be easily breakable with software anybody could readily download from the internet. All a hacker had to do was “listen in” on wireless communications for a time, and the software would analyse the packets and eventually figure out the encryption key. WPA implemented a rotating encryption key as opposed to WEP’s fixed key, so that such attacks no longer work.
WPA2 implemented additional encryption and security modes on top of WPA, while just last year WPA3 was certified, which implements new protections against weak passwords and during the initial handshake while also increasing the encryption level in enterprise devices.
Most routers today come with WPA2 on by default (very few have WPA3 yet), which is fine for home use.
Changing the password is also important, since default passwords are a major weakness in many home appliances – including routers. It’s how the massive VPN Filter virus spread last year – by infecting routers that still used their default passwords (though that related to admin passwords rather than Wi-Fi passwords).
Your router, mesh point or wireless access point might not be secure by default.
Even if your router came with a unique password (as many now do), it’s still worth personalising it. The router vendor might have a system for generating default passwords that is known or hackable, and attackers might exploit it. The only way to be sure that your password can’t be guessed is to create your own good password.
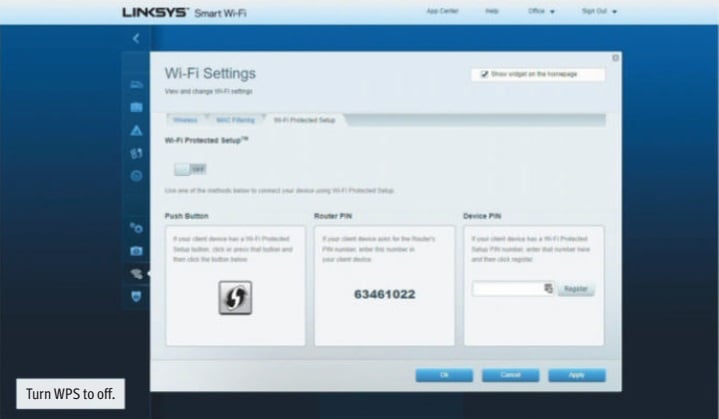
DISABLE WI-FI PROTECTED SETUP (WPS)
Wi-Fi Protected Setup (WPS, not to be confused with WPA) was designed to be a simple means to connect wireless devices with networks without having to know a password. It commonly works somewhat like Bluetooth pairing – you press a button on the router and the wireless device (or a software button on a computer) and the device will automatically “pair” with the wireless network – which is to say that the router will send the password to the device.
Unfortunately, major flaws were found in the implementation of WPS, and devices that use it are potentially open to exploitation. Despite that, many routers still ship with it turned on by default, so it’s a good idea to take the time to turn it off if you can.

NEARLY ALL MAJOR VPN SERVICES HAVE APPS FOR BOTH PC AND MOBILE, SO SETUP IS GENERALLY PRETTY EASY AND YOU’LL RARELY EVEN NOTICE IT’S ACTIVE – BUT ATTACKERS WILL.
It doesn’t matter which country you connect to (although for speed reasons you might want choose an Australian server).
To do that, find the wireless settings in the administration console of the router. You may have to use the web console – which means opening your web browser and logging into your router the old fashioned way. Many mobile control apps might not have the option to change the WPS settings. Find the WPS setting and turn it to off.
WHY THIS IS IMPORTANT
In 2011 a major security flaw was found in WPS. Every WPS device has a fallback PIN authentication method – designed so that devices could be authenticated just by typing in the WPS PIN number of the other device you’d like to pair with.
This PIN is seven digits long, plus an extra digit that serves as a checksum, which means that theoretically there are 10,000,000 possible pin numbers; it would likely take months for a hacker to brute force the pin by trying every number.
However, a researcher found that if you guess four digits of the number correctly, WPS would confirm that those numbers were correct. So you only had to make 10,000 guess to get four digits of the code; and another 1,000 to guess the other three digits. With software a hacker could potentially crack that in a few hours and access with your network.
There has been some mitigation of this attack in recent router firmware revisions – most commonly a longer timeout after a wrong pin number to slow down hackers trying to brute force the number – but it is still a vulnerability. And let’s be honest: you’re not really losing anything by foregoing this old system – have you ever actually used WPS?
USE A VPN ON PUBLIC NETWORKS
This last point is less about how you configure your own wireless network and more about how you behave when connected to other people’s networks – particularly public Wi-Fi networks such as those you’d find in a hotel or a McDonalds.
If you’re connected to a public Wi-Fi network, always use a VPN service. This rule applies to both PCs and mobile devices.
If you don’t subscribe to a VPN service, there’s a variety of free ones available. Most free VPN services do have data limits, but if you’re only using it when connected to public networks, you’re unlikely to go over the limit. Nearly all major VPN services have apps for both PC and mobile, so setup is generally pretty easy, and you’ll rarely even notice it’s active – but attackers will.
WHY THIS IS IMPORTANT
When you’re on a public wireless network, you’re vulnerable to certain types of “man in the middle” attacks. One possible attack is where a hacker sets up a fake Wi-Fi hotspot, physically closer to you than the real hotspot. Your computer, getting a stronger signal from the fake hotspot than the real one, will connect to it. Now all your internet traffic flows through the computer of an attacker – and they can read anything that isn’t encrypted as well as monitor which sites you visit and your other online activity.
A VPN prevents that. You’ll still be connected to the fake network, but all you data is encrypted and no metadata (such as which sites you visit) will be visible to the hacker. The only connection they will see is between you and the VPN service provider, and all the data flowing across that connection will be encrypted so they can read none of it. Essentially, the joke is on them.





