Have you been hacked?
THE EXPERT GUIDE TO SECURING YOUR DIGITAL ECOSYSTEM. WINDOWS, MAC, android, online & much more

We reveal the tips and techniques you need to lock down your entire digital ecosystem.
THE BEST windows SECURITY SUITES: We uncover the best security suites for all types of Windows users.
SECURITY ON ANDROID: Everything you need to know about securing your Android phone or tablet.
SECURITY ON MAC: How to stay safe when using your Mac at home or on public Wi-Fi hotspots.
LOCK DOWN FACEBOOK: Facebook is great for sharing, but it’s easy to overshare — it’s time to control who sees what.
GIVE YOURSELF A GOOGLE PRIVACY CHECK: How to stop Google from tracking your online activity.
STOP WINDOWS 10 Spying: The Creators Update has changed-up Windows’ privacy options again, so we show you how to lock them down.
Secure your digital ecosystem

Worried about your online and offline security and privacy?
Nick Peers reveals the tips and techniques you need to lock down your entire digital ecosystem.
There’s hardly a day goes by without some new hacking controversy. From online sites getting compromised to people facing down ransomware demands, the always-connected era is one fraught with danger. Prevention is always better than cure, so what can you do to ensure you’re as protected as you can be?
In this feature, we’re going to arm you with all the tools, tips and guides you need to close the door on drive-by hackers, malware and other online threats to your privacy and security. We’ll start by locking down your PC — ensuring your security software is up to scratch, you have a firewall that’s fit for purpose and that your personal data is encrypted and as difficult to steal as possible.
Next, we’ll look at tightening the security of your home network — you’ll discover how to log on to your router, improve the security of your Wi-Fi network and restrict access to only those devices you explicitly choose. We’ll also show you how to perform a quick security sweep of your wireless technology and check it for weak spots.
Then it’s on to your internet connection — you’ll learn how to encrypt your connection using a VPN, even when browsing in public spots, and discover how to engage in secure web browsing, email and even chat. Last, but not least, you’ll learn how to implement a foolproof — and watertight — password management system to ensure you have unique, strong passwords without making things awkward. We’ll even show you how to switch on two-factor authentication for even greater protection.
Follow these tips and you’ll lock out the snoopers and hackers, and keep your personal data as private and protected as it can be. It’s time to fight back.
Secure your cloud backups
If you back up data to the cloud, you may be concerned about its security.
All cloud providers promise to encrypt your data for privacy purposes, but what kind of encryption is provided, and where are the keys required to decrypt your data stored? If you’re at all paranoid, you will want those keys kept in your personal possession, a technique which is known as client-side encryption. Sadly, not many cloud backup providers offer this — neither Dropbox nor OneDrive do, for example.
If this is a concern, you can encrypt your data locally before uploading it to the cloud — if you’re already using VeraCrypt, for example, you could simply create an encrypted volume inside your cloud folder and store all sensitive data in there. On the other hand, if you primarily use your cloud provider for syncing data between your various devices, you’ll need to choose a solution that enables you to access your data on whichever platforms you need.
There are a number of options out there, but one that’s unlimited and free for personal use is nCrypted Cloud (www.encryptedcloud.com/apps/windows). Once installed, set up your free nCrypted Cloud account, then connect cloud providers (Dropbox, OneDrive, Box and Google Drive are all supported) and finally choose the folders that you want to encrypt. If you want access from other computers or mobile devices (Mac, iOS and Android are also supported), then simply install the relevant app or program, link it to your nCrypted Cloud account and you’re done.
Tighten up your Windows security
Step one in protecting your home starts with your own PC.
Let’s begin by tightening the security of the computers in your home. First, take a look at your security software.
If you’re currently using Windows Defender, we recommend that you switch to something stronger.
If you’re happy to rely on free protection, then Avira Free Security Suite (www.avira.com) is an excellent choice. It’s light on its feet, easy to use and gives you protection that matches many commercial products. It includes anti-malware, system tune-up, a cloud-based password manager, secure browsing, a volume-limited VPN, web and search filter, as well as a software update checker. Plus, you can manage multiple devices from a single desktop.
Paid-for protection from the likes of Kaspersky, Symantec and Norton goes even further, and you can get discounts by buying multi-computer licences to cover your whole household. If going down this route, keep an eye out for frequent deals — you can purchase these any time of the year, then apply them once your subscription has run out.
SECURE YOUR FIREWALL
If you decide to use free protection, you’ll be relying on the Windows Firewall. It has all the tools you need to close the door to hackers, but it doesn’t use them fully. Windows Firewall monitors incoming traffic from your network and the internet for potential threats, but waves through all outgoing traffic from applications without a second thought.
If you don’t have a third-party firewall installed, then TinyWall (tinywall.pados.hu) gives you a way to use Windows Firewall as a two-way firewall. True, it needs a bit of configuration to get working, but our step-by-step guide on the opposite page reveals all. The only caveat is that it can take some time before all your software is working correctly — look out for failed updates and applications complaining about not having enough access. If you recognise and trust the app in question, simply follow the guide to add it to TinyWall’s whitelist.
Also note the potential issues with sharing files and printers with other people — you can work around most of them, but if it’s too much hassle, look for a paid-for solution instead.
“If you decide to use free protection, you’ll be relying on the Windows Firewall. It has all the tools you need to close the door to hackers, but it doesn’t use them fully.”|
ADD MORE PROTECTION
Whatever security software you have installed, there’s always room for extra help. You can start by installing Malwarebytes Anti-Malware Free (www.malwarebytes.org), which can root out and remove infections missed by your main security software.
The free version should be used to scan your system at least once a week, or pay for the Premium version for real-time protection (without conflicting with any of your other security tools).
If your security software doesn’t offer any protection against ransomware, then install BitDefender Anti-Ransomware Tool (www.bitdefender.com/solutions/anti-ransomware-tool.html) to block four known ransomware families. Ransomware is particularly nasty malware that encrypts all the data on your hard drive, demanding you pay a hefty ransom in return for the key required to unlock it — which also relies upon the honesty of the criminal behind it. Another way to protect yourself is to regularly back up your data both offsite (the cloud) and onsite (an external hard drive).
PROTECT YOUR DATA
Personal files are priceless, but they’re also sensitive. If you’re a laptop user who takes their PC on the road, you should ask yourself how you would feel if your laptop was stolen. The answer is to encrypt your files, and that can be done a number of ways depending on where the data is stored.
If you’re carrying files on a USB thumb drive, the easiest way is to create an encrypted ‘container’ into which you place your most sensitive files. The container is passwordprotected — supplying the correct password unlocks the files within as a virtual disk drive, but otherwise, they remain hidden and scrambled.
If this approach appeals, take a look at Rohos Mini Drive (www.rohos.com/products/rohos-mini-drive). This lets you to create virtual drives up to 8GB in size for free.
If you want to encrypt your entire machine, then Windows 10 Professional users should type “bitlocker” into the Search box to find out how to use Windows’ own encryption tool. If you’re running Windows 10 Home, then use VeraCrypt (veracrypt.codeplex.com). You can use it either to create encrypted volumes of locally-stored data or encrypt entire drives and partitions — see the ‘System Encryption’ section of VeraCrypt’s documentation.
Lock down your network
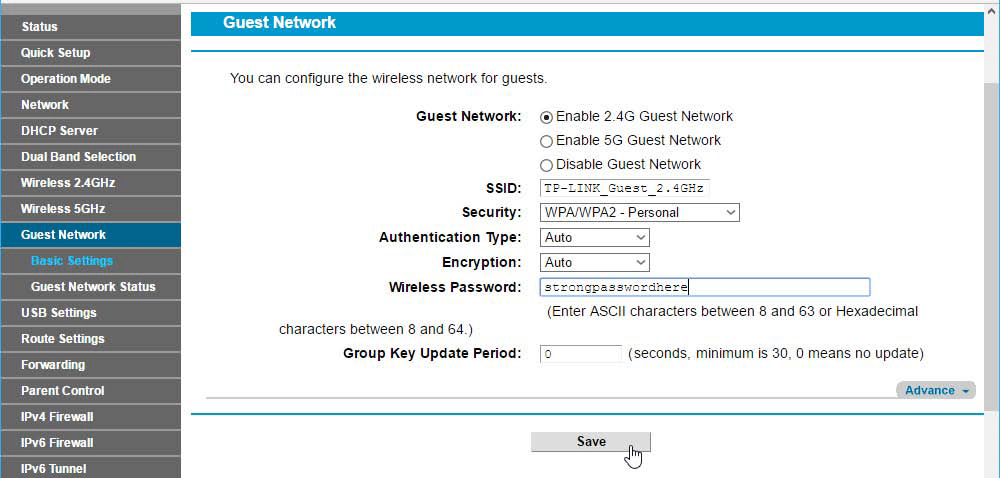
Stop hackers and snoopers from accessing your router.
Even if you’ve yet to embrace the concept of the smarthome, the chances are you will still have a number of devices, as well as your PC, competing for bandwidth on your home network. Read on to discover how to reduce its vulnerability with a home network security audit.
LOCK YOUR ROUTER
Let’s start with the gateway between your home and the internet. If you’ve never carried out admin on your router before, then you will definitely find ways in which to strengthen its security. You can usually manage your router through your web browser by entering its four-digit IP address into the Address Bar. To do that, first open ‘Settings > Network and Internet’ and click ‘View your network properties’, then make a note of your router’s IP address under Default Gateway.
Protect your laptop’s data from theft by encrypting its entire storage drive
Type the IP address into your browser, and you will now see a status or login page. Each router handles things differently, but they all follow a broadly similar pattern. Consult its documentation, look on the router box or visit its support website for the default login details to gain access.
It’s possible for drive-by hackers to target routers remotely, relying on users having left the default password in place, so if that’s the case on your router, you should look for the option to change this — on our TP-Link router it’s under ‘System Tools > Manage Control’, but other routers will vary. See page 52 for tools that can help you help create a strong password.
PROTECT YOUR WI-FI
Once the router password has been changed, it’s time to tighten up your Wi-Fi network. Your router should have already set encryption (WPA2-PSK with AES encryption ideally), but it’s a good idea to change the default password. Yes, you’ll have to reconnect all your wireless devices, but you’ll immediately kick off any unauthorised devices who might have been using it without your knowledge. If you have separate 2.4GHz and 5GHz networks set up, repeat for both (and consider setting unique passwords for each separate network).
Each computer or device on your network is identified using its MAC address, a six-digit hexadecimal code.
If your router supports MAC filtering, it means you can lock down your wireless network even further, by only accepting connections from devices with specific MAC addresses.
First, you need to identify the MAC address for each device you own, which we recommend you write down and record somewhere secure. You’ll need to look up instructions for your specific device, but it’ll typically be under Settings somewhere. In the case of your wirelessly connected PC, look under ‘Settings > Network and Internet > View your network properties’ in the Physical Address (MAC) section.
Once you’ve got all the MAC addresses you need — including, critically, your wireless PC if applicable — enable MAC address filtering and enter the addresses one by one. If prompted, choose the option to only allow devices with MAC addresses that match.
If you frequently allow family and friends to access your Wi-Fi network, enabling MAC address filtering may be a step too far. That said, explore your Wi-Fi router’s settings to see if it offers a guest network function — if it does, you can give visitors internet access without opening up the rest of your network to them. Make sure that you enable the WPA/WPA2 encryption option for the guest network, and set a unique wireless password for your guests to use.
More security settings
Your devices connect to the internet using a series of virtual ports, with different ports used by different applications and services.
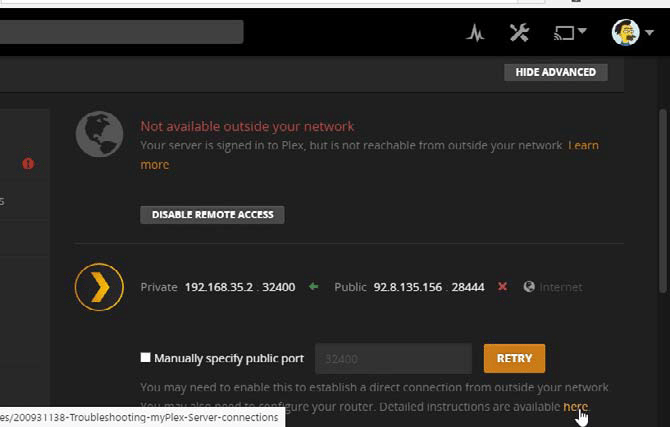
Some are standardised — for example, port 80 provides connections to the web, while port 25 is used by SMTP email servers — but others are allocated on an application-by-application basis (if you want to access your Plex Media Server over the internet, for example, you need to connect through port 32,400).
In the past, you had to manually open ports through your router’s setup utility, but thanks to the arrival of Universal Plug and Play (UPnP), apps can now communicate effortlessly with your router and open the ports they need in the background.
While convenient, this does open your router to potential breaches (malware can open ports to wreak havoc, for instance). You should, at the very least, check periodically to see which apps have access to your router and if you don’t recognise any, disable it immediately to close all ports.
You can then investigate the dubious app further using the IP address to target the device it’s originating from before deciding whether or not you should re-enable it.
A better approach — if a bit less convenient — is to manually set up port forwarding yourself. Apps should alert you when this needs to be done, and you can follow the step-by-step guide at the bottom of this page to see what information needs to be set up for each port.
One final thing: check your router’s support website to see if any firmware updates are available for it. These can add more features, but may also contain security fixes. Installing an update usually involves downloading the update file to your PC, then uploading it manually to your router’s configuration utility where it’s then applied. Be sure to back up or record your settings before doing so, in case the update wipes them out.
You should, at the very least, check periodically to see which apps have access to your router and if you don’t recognise any, disable it immediately to close all ports.
Protect home network kit
You’ve tightened your router settings, but what about the devices connected to your network?
The growth in smarthome tech means many more wireless devices are now communicating over the internet, so make sure these are locked down, too. We’ll show you how to use strong passwords and other measures to lock down any account settings screens over the page, but you should look out for firmware updates that can help close security loopholes.
If you have a webcam attached to your PC, make sure it’s not in a place where it could be used to spy on you. Keep an eye on the activity light — it should only be on when you’re using it. If the camera is a USB model, consider unplugging it when not in use or at least cover the lens, so even if it is compromised, it won’t see anything. If you use a security camera, protect it with a strong password and limit who has access. You should also switch on its notifications to make sure you’re alerted whenever it’s used.
If you’d like to see what’s currently connected to your home network — potentially enabling you to spot snoopers or hackers — download and run Advanced IP Scanner (www. advanced-ip-scanner.com). It will list all currently active network devices. Use the Manufacturer field to help identify unknown devices if the name doesn’t give you any clues, and keep scanning from time to time.
Open up ports manually.
1 CHECK OUT AN APP’S INTERNET NEEDS
Any app on your computer (or other device) that needs access to the internet should make it clear what you need to do in order to open up access to it. You should start by looking into the program’s own settings to find out where you determine which ports it requires and the steps you need to follow to make it work.
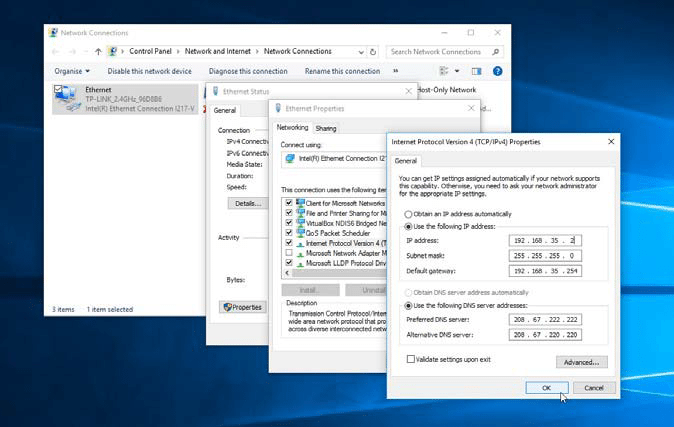
2 set static ip address
If you’ve not already done so, you’ll need to set up a static IP address for the device that is running the application. In Windows 10, you should follow the guide at portforward.com/ networking/static-ip-windows-10. htm. Make sure that you give the device an IP address which doesn’t clash with your router’s DHCP server.
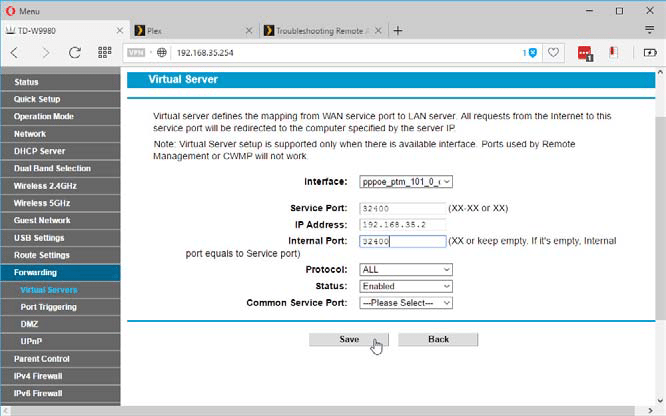
3 ADD new port
Armed with the instructions provided in from the site in Step 2, locate the port forwarding section of your router’s configuration utility. Now create a new port, entering the port number into both port fields and your device’s IP address into the IP Address field. Click Save or Enable to test the connection and see if it’s working correctly.
Protect yourself online
Boost privacy and security when using the internet.
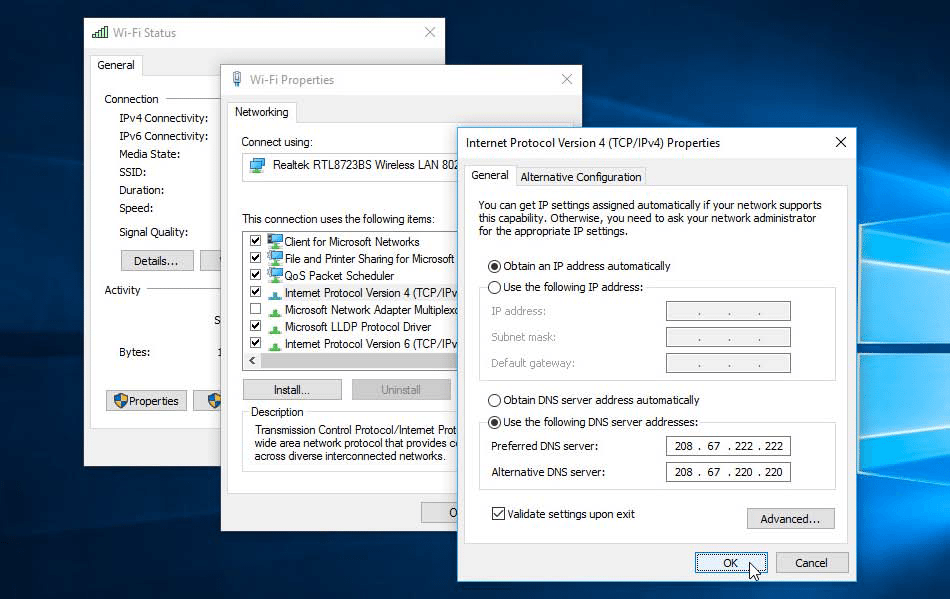
Now let’s make your internet connection more secure, starting with your DNS server. This is used to translate web addresses into their physical IP addresses. Normally, your DNS server is provided by your ISP, but it’s not the best choice for performance and security reasons. Alternatives such as OpenDNS are faster, more reliable and, crucially, apply more security checks to validate web addresses. With OpenDNS, you can sign up at its website (www.opendns. com) for things like parental controls and identity theft protection.
Alternatively, log in to your router, locate where its DNS settings are stored, and then change them to the following addresses: 208.67.222.222 and 208.67.220.220. The effect will be immediate. If you lose your connection, check that you’ve added them correctly.
If you have any devices you use away from home, you can change their DNS settings to OpenDNS, too — in the case of a Windows 10 PC, you need to type “network” into the Search box and click ‘View network connections’. Double-click your adapter’s entry and click Properties, then select ‘Internet Protocol Version 4 (TCP/IPv4)’ and click Properties. Select ‘Use the following DNS server addresses’ and enter 208.67222.222 and 208.67.220.220 into the two boxes, then click OK.
SECURE WIRELESS CONNECTIONS
When you’re on the go, it’s tempting to connect to any public wireless hotspot, even ones that don’t ask you for a password. The problem is, these are often completely open, allowing anyone to eavesdrop on you. That’s where a VPN comes in.
A VPN creates a ‘tunnel’ through a public network, that enables you to connect to the internet, with all the traffic to and from your device encrypted. If you just want to browse the web, install the Opera web browser (www.opera.com), which includes its own VPN. Look for the VPN button in your Address Bar (you can enable it via ‘Menu > Settings > Privacy & security’). Click it, flick the switch to ‘On’ to encrypt your web browsing. If you want to widen VPN support to all your network traffic, the simplest solution is to install CyberGhost VPN (www.cyberghostvpn.com), which can encrypt your entire connection. The free version is unlimited, but slow — pay the US$10.99 monthly fee for faster performance.
MORE SECURE WEB BROWSING
Your internet connection may now be secure, but you can still do more. Opera comes with its own built-in ad blocker, which can help you avoid adverts as well as malware, but if you are using another browser, install the Adblock Plus plugin instead.
It’s also a good idea to connect securely to websites when you can, using the ‘https://’ protocol rather than the insecure ‘http://’ one. Remembering this is tricky, so install the open-source Smart HTtPs add-on, and it will try to connect securely.
Half of the trick of staying safe online lies in avoiding dodgy websites. While web browsers are smarter at detecting and diverting you from sites that are known to be dangerous, there’s always room for improvement. See what web-filtering tools your security software offers in the form of a browser toolbar and use it to search the web instead of Google.
Similarly, be careful with software downloads — get them from a reputable website and scan the file with your anti-malware tool before running it. Exercise similar caution with browser add-ons — review each one before you install it, and periodically check which add-ons have been installed, removing any you no longer need or recognise.
It’s a similar story with email. Avoid clicking any links and instead type the URL into your web browser directly to ensure you end up going where you think you should. You should also scan email attachments before opening them, and employ the services of tools such as Mailwasher (www.mailwasher.net) or PopTray (www.poptray.org) to screen messages before they land.
Emailing someone is akin to sending a postcard — anyone can read it. If you use Thunderbird, check out the step-by-step guide to find out how to encrypt email.
Chat securely
Do you often stay in touch through instant messaging apps such as Skype?
While they can be great fun, the bad news is that Skype, in particular, isn’t that secure. If you want true end-to- end encryption for voice, video and text-based chats (as well as secure file sharing), then you’ll need to look into using an alternative solution.
The most secure we have found is Retroshare (www.retroshare.net). The only catch is that you’ll have to convince all your contacts to use it, too — if this is a deal breaker, take a look at Jitsi (jitsi.org), which supports a number of different messaging platforms.
You can install Retroshare (choose the QT5 version when at the download page) to your PC’s main storage drive or run it as a portable application, then set up your account and get each contact to do the same. You then export certificate files to send to each contact before importing their file in turn. Tick ‘Authenticate friend (Sign PGP Key)’ if you’re confident in their identity, then wait while Retroshare’s Connection Assistant sets up the connection.
It’s a fiddly process getting that initial connection set up (and you have to repeat it for each device you install Retroshare on and import your identity into), but once both of you are verified and connected to the other, you can be secure in the knowledge that future chats aren’t just encrypted and secure from unwanted eavesdroppers, but that you know exactly who you’re chatting with.
Beef up your passwords
How to lock down your online and offline accounts.
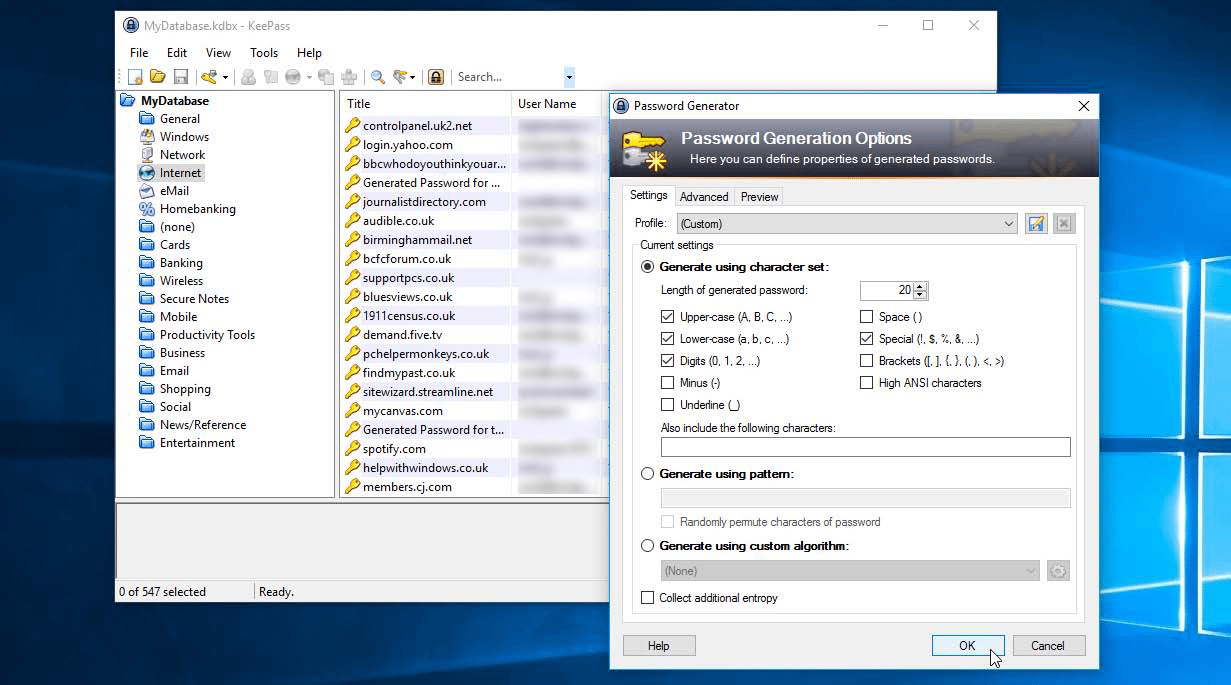
Do you rely on a limited number of passwords to secure accounts both online and off? You’re not alone.
The sad truth is, though, that this represents an opportunity for hackers and identity thieves who, once they crack one of your passwords, can often crack them all.
The way to solve this problem is to create unique, complex passwords for each account that you use, using a mix of upper and lowercase characters, numbers and even symbols. The trick then is remembering them all.
The solution lies in employing the services of a password manager.
A good password management tool will generate strong random passwords, make them easy to access and protect them all behind a single, strong master password you can remember. You log into the password manager with the master password, and the rest of your passwords are then available.
PICK A PASSWORD
If you’re super-concerned or even paranoid about security, you’ll want to store your passwords offline, in which case you should look at KeePass (keepass.info). Everything’s stored locally, and you can add an extra layer of protection to your passwords by locking them using both a master password and a key file, which you store on an external disk or drive.
A good password management tool will generate strong random passwords, make them easy to access and protect them all behind a single, strong master password you can remember
It’s portable too, so you can store everything on a USB thumb drive and take your passwords with you on to other computers.
The biggest drawback with KeePass, however, is that it only works on your PC — if you want access to your passwords on your mobile, for example, then you’ll need to be within reach of your machine to access them. If you’re willing to store your passwords in the cloud (encrypted, of course), a more convenient option is to use a tool such as LastPass (www.lastpass.com).
LastPass offers a similar feature set to KeePass, minus the key file option. Instead, what it gives you is more convenience — you can install apps on your devices (including mobile ones) and use browser plugins to make it easier to log into sites — see the guide on the opposite page — as well as generate strong, random passwords for new accounts. LastPass works with any service you access through your web browser, making it a good fit for your router, plus locally hosted servers such as Plex.
LastPass also offers secure notes and form filling tools, for storing other sensitive information. You can also ask LastPass to prompt you for your master password each time you open a particularly sensitive note. It also includes a security audit, which checks all your passwords for weak ones, duplicates, passwords you haven’t updated in a while and even accounts known to have been compromised.
All of this functionality — including syncing across mobile and desktop — is now completely free. Upgrade to the LastPass Premium package (US$24 per year) for more features, such as LastApp — a tool for using LastPass in conjunction with installed apps or programs on your device.
Two-factor authentication and two-factor verification add an extra layer of security, by checking your identify using mobile devices.
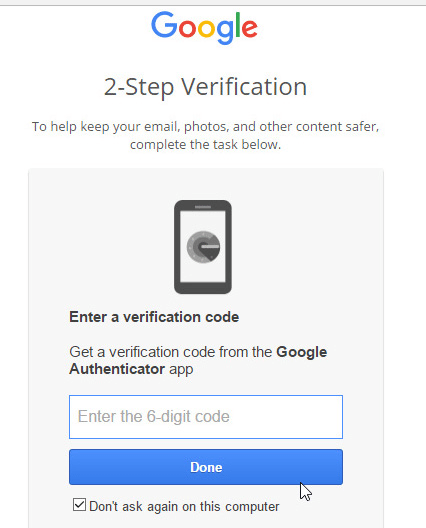
Two-factor authentication and two-factor verification add an extra layer of security, by checking your identify using mobile devices.
MULTI-FACTOR AUTHENTICATION
Even the strongest password can be guessed or cracked, so what happens if your password is leaked? The solution is to implement two-step verification or two-step authentication. This adds an extra step when logging into key accounts (including LastPass) on new devices. This can be as simple as an email notification, or you can implement a solution that requires your mobile phone or tablet to be at hand.
This latter option is best, because you’ll need physical access to your mobile device in order to verify the request. Here, you can opt to receive a code via text message, or you can install a special authentication app that generates codes offline that are tied to your account. If you’re using LastPass to protect your passwords, install the free LastPass Authenticator app to provide these codes — not only can you then switch on two-factor authentication for services and accounts that support it, but you can switch it on for LastPass, too, making it even more secure.
You can find out if your chosen service supports two-factor authentication by logging into it and exploring the security section of its settings — LastPass users should log into their account at www.lastpass.com and go to ‘Account Settings > Multifactor Options’, for example. From here, you can pair it with the free LastPass Authenticator app.
Other services make it relatively easy to add multi-factor authentication using LastPass Authenticator (if you can see an explicit reference to it, then choose the Google Authenticator option) by providing you with a QR code to scan into LastPass Authenticator using your mobile’s camera, which then automatically pairs your account with the app.
One tip for additional security: what happens if your smartphone or tablet gets stolen? Make sure you tap Settings in LastPass Authenticator and flick the ‘Use PIN Code’ switch to ‘On’ to protect it with a six-digit PIN. And remain wary of unexpected requests to use the authenticator app — it may indicate that a hacker has got your password and is hoping you can be tricked into verifying their request for access.
Other alternative password managers include lPassword (1 password.com) which works across all your devices including Windows, Mac, Android and iOS. It also offers a web browser plugin.
One-time app passwords
When you enable two-factor authentication, logging into the account on a new device or application should trigger a prompt to confirm your identity, but some older devices and apps — including email apps Thunderbird and Outlook — don’t work nicely with it.
The good news is you don’t need to source a separate app or compromise your security — most services that offer two-factor authentication offer what’s known as one-time passwords. These are passwords you can use in place of a regular password to log into an application or device. If an app refuses to work properly even after entering the correct password, try one of these instead.
If you’re a Google user, for example, go to accounts.google.com and sign in. Choose your username, then ‘My Account’. Click ‘Sign-in & security’, scroll down and click ‘App passwords’ beneath ‘2-step Verification’. Choose ‘Select app’ to give your app a name, and a device, then click Generate. Copy and paste the password into the relevant field (tick the option to save it). Now all should be well…
Secure your web logins
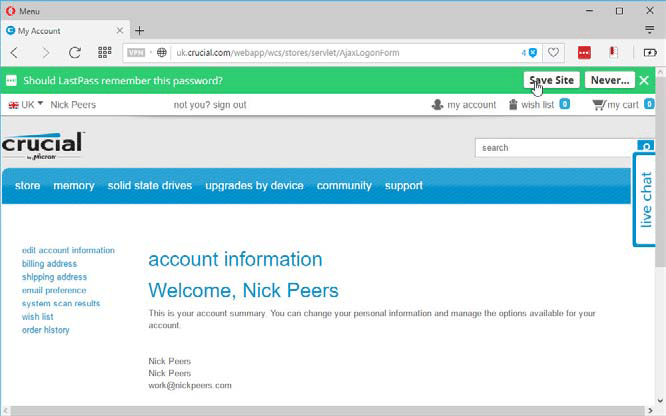
REMEMBER LOGINS
Once you’ve installed LastPass, browse to a website and log in using its username and password in the usual way. After logging in, LastPass will pop up a green bar offering to save the website’s credentials for you. Do so, and when you next visit the site, you’ll see a LastPass button appear in the login fields — click this to fill your details in quickly.
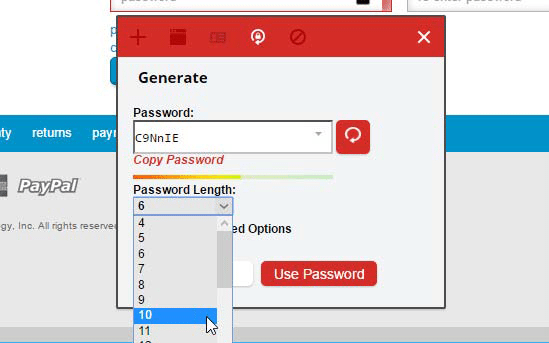
UPDATE PASSWORDS
If an existing password you use is a weak one, go to your account’s settings and look for an option to update your password. Click the small padlock button next to the password field to generate a new random password. Be sure to set the password length to longer than the default six characters — 10 or more characters is usually best.
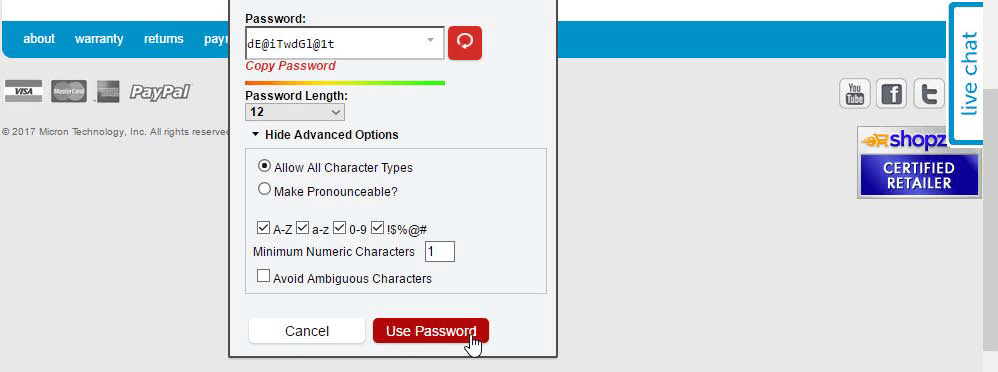
GO ADVANCED
Click ‘Show Advanced Options’ and tick the symbols box to increase your password strength further. Once you’re happy with it, click ‘Use Password’. You’ll be prompted that the password has been generated, so click ‘Yes, use for this site’, then save your changes to update both the account and LastPass. Congratulations! Your password is now more secure.